A multi-million dollar data breach isn't just a headline, it's a real threat that can sink a business. The total cost of a data breach goes way beyond the initial cleanup, hitting you with hidden fees, lost customers, and regulatory fines. We help you find and fix security holes with fast, affordable pentesting so you can avoid that disaster.
Breaking Down the True Cost of a Data Breach
When a data breach happens, the costs start piling up almost immediately. You can think about it in two main parts. First, there are the obvious direct costs, like hiring security experts to figure out what went wrong and fix the immediate issue.
Then there are the hidden costs, which usually hurt the most over time. This includes losing customers, long term damage to your reputation, and legal or regulatory fines. The true cost of a data breach is a messy combination of both.
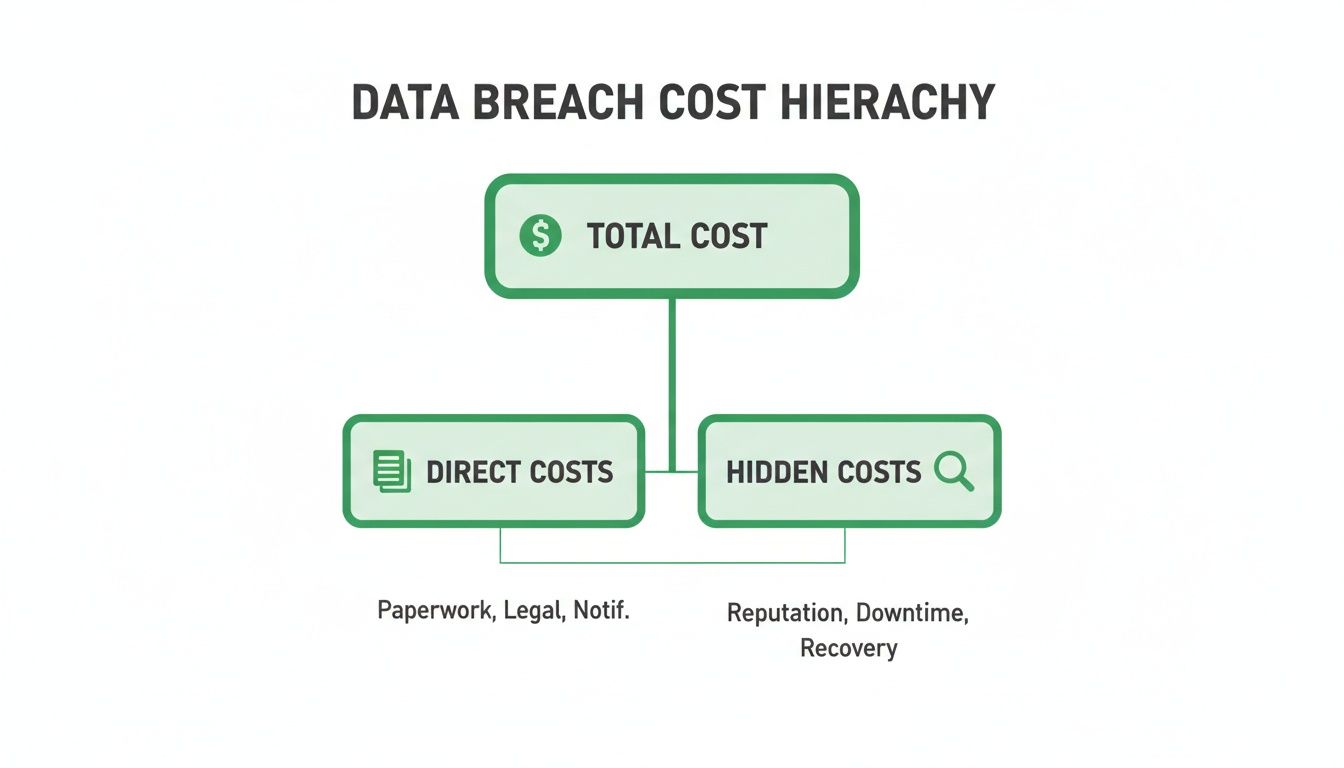
This is why the financial pain often lasts long after the technical problem is fixed. A breach does not end when systems are restored. It can impact sales, partnerships, and trust for years. A data breach is rarely a single event, it is the start of a long and expensive recovery process.
Why Data Breach Costs Are So High
So what do the numbers actually look like. The global average cost of a data breach is around $4.44 million. Companies have improved at detecting breaches faster, which helped bring that number down slightly.
In the United States, however, the average cost jumps to about $10.22 million. The reason is strict government fines, complex state privacy laws, and aggressive enforcement against companies that are not prepared.
Once legal costs, customer notification, and lost business are added up, breach expenses grow fast.
A Simple Look at Data Breach Expenses
To really get it, let's look at where the money goes. This table breaks down the main costs you would face after a breach.
Expense CategoryWhat It Typically IncludesDetection & EscalationForensic investigators, internal security team overtime, assessment tools, and crisis management team activation.NotificationLegal counsel to determine who to notify, creating contact lists, postage or email service costs, and call center support.Post-Breach ResponseCredit monitoring services for victims, identity theft protection, public relations campaigns, and regulatory communication.Lost BusinessCustomer churn, reputational damage leading to fewer new clients, system downtime, and business disruption.
This is why having a solid data breach response plan before an attack is so important. A good plan helps you act fast, limit the damage, and keep those costs from spiraling out of control.
How Attackers Drive Up Your Recovery Costs
To defend your organization, you have to think like an attacker. Most breaches are not loud or obvious. Attackers usually start with simple tricks to get inside without being noticed.
The way an attacker gains access has a huge impact on cleanup costs. The longer they stay hidden, the more expensive the breach becomes. Each day inside the network gives them more time to steal data and cause damage.

Unlocking the Doors Through Phishing Attacks
Phishing remains one of the most common entry points because it works. Attackers send emails that look legitimate and trick employees into clicking malicious links or handing over credentials.
Once a password is stolen, attackers can move freely inside systems. A single compromised login can turn into a massive and very expensive breach.
When the Threat Is Already Inside
Sometimes the threat comes from inside the organization. A malicious insider, such as a disgruntled employee, can cause serious damage because they already have legitimate access.
They know where valuable data lives and how systems work. These breaches are costly because activity often looks normal at first, allowing data theft to go unnoticed for a long time.
The Problem with Stolen Login Credentials
Another common attack method involves reused or stolen passwords. Attackers buy credential lists from past breaches and test them against company systems.
If an employee reused a password, the attacker can log in without triggering alarms. Weak password policies leave the front door open. This is why OSCP, CEH, and CREST certified pentesters are valuable. We think like attackers and find these gaps before they are exploited.
Why Every Day of Delay Costs a Fortune
When a breach occurs, time is money. The period between initial access and removal of the attacker is known as the breach lifecycle. The longer it lasts, the higher the final cost.
It is similar to a small leak in a roof. Fix it quickly and damage is minimal. Ignore it and the repair bill explodes. Delays turn manageable incidents into financial disasters.

The High Price of a Long Breach
Data shows that breaches resolved in under 200 days cost over $1 million less than those that last longer. When attackers remain inside networks for months, they steal more data and cover their tracks.
Many organizations fail because they miss early warning signs. A single phishing email can lead to months of quiet activity before anyone notices.
Breaking Down the Breach Timeline Stages
The breach lifecycle includes identification and containment. Delays in either stage increase damage.
Identification is how long it takes to realize a breach happened. Containment is how long it takes to remove the attacker and close the entry point. Slow responses in either phase raise costs quickly. This is why strong incident response planning matters. Check out our guide on creating a security incident response plan.
How Fast Pentesting Slashes Your Risk
Proactive security reduces these risks. Penetration testing helps identify weaknesses before attackers do.
OSCP, CEH, and CREST certified testers simulate real attacks to find flaws automated tools miss. Instead of just listing problems, we explain how to fix them. Reports are delivered in under a week so teams can act quickly.
How Your Industry Shapes Breach Costs
Breach costs vary widely by industry. Healthcare breaches are far more expensive than retail breaches because of the sensitivity of the data involved.
Industries handling medical records or payment information face stricter regulations and heavier fines.
Why Healthcare Breaches Cost The Most
Healthcare breaches average around $9.77 million per incident. Patient data is extremely valuable, and regulations like HIPAA carry serious penalties.
Breaches require notifying every affected patient, providing credit monitoring, and responding to government investigations. This combination drives costs higher than almost any other sector.
Financial and Tech Industries Also Face High Stakes
Financial organizations face average breach costs of about $6.08 million due to standards like PCI DSS. Failure to protect card data can trigger major fines.
Technology companies are close behind, with average costs around $5.45 million. They store valuable intellectual property and customer data that attackers want. See our guide on HIPAA compliance for small businesses in our detailed guide.
Meeting Compliance Rules on a Budget
For founders and IT managers, compliance is not optional. Regulations like SOC 2, HIPAA, and PCI DSS require regular testing.
Traditional pentesting firms are often slow, expensive, and inefficient. We offer an affordable alternative. Certified testers deliver fast manual pentests with audit ready reports in under a week.
Lowering Breach Costs with Penetration Testing
The best way to avoid massive breach costs is to find weaknesses early. Penetration testing does exactly that by simulating real attacks. Certified ethical hackers attempt to break into systems using attacker methods. This gives a realistic view of actual risk.
The Clear ROI of Proactive Pentesting
A pentest costs a fraction of a breach. Spending a small amount now prevents multi million dollar losses later.
You get a clear map of weaknesses and a plan to fix them. It is the difference between preventive maintenance and emergency recovery.
Why You Need a Human Perspective
Automated scanners catch common issues but miss creative attack paths. Real attackers are human and adaptive.
Manual pentesting mirrors this behavior. Certified experts find vulnerabilities automation cannot, providing a true picture of security posture.
Affordable Pentesting That Is Actually Fast
Traditional pentesting is slow and expensive. Reports often take months. Our approach is built for speed and efficiency. Full reports are delivered within a week, allowing teams to fix issues immediately. You can learn more about our pricing on how much a pentest should cost in our guide.
Your First Step Toward a Stronger Defense
Waiting for a breach is not a strategy. Security is more affordable and straightforward than most businesses think.
The first step is understanding your weaknesses so you can fix them before attackers find them.
Your Path to Better Security Is Clear
Getting started doesn't require a huge budget or a long project. Our process is designed to be fast, affordable, and effective. We give you exactly what you need without the high costs and long waits of other firms.
Our team of OSCP, CEH, and CREST certified pentesters delivers a full, actionable report in under a week. This lets you fix your security issues quickly and meet compliance deadlines without slowing down your business.
Stop Guessing About Your Security Risks
Hoping a breach won't happen is a recipe for disaster. The high cost of a data breach is a real threat that can shut you down. You need a solid plan for modern data breach prevention to protect yourself.
The best thing you can do right now is find and fix your security holes. Our manual pentesting gives you a real-world view of your weaknesses and a clear plan to fix them. Ready to see how easy and affordable it is to get started? Reach out through our contact form for a quick, no-nonsense quote.
Got Questions About Data Breach Costs?
We get a lot of questions from IT managers and founders about data breach costs. Here are simple answers to the most common ones.
What's the Biggest Driver of Breach Costs?
Time. The longer an attacker is in your network, the more it costs. A breach found in under 200 days costs over $1 million less than one that drags on longer.
Every second matters. A slow response means more stolen data and a bigger cleanup bill. This is why we are so focused on speed, delivering our pentest reports in under a week so you can act fast.
Is Proactive Security Really Worth It?
Yes, absolutely. You can either pay a small amount for a pentest now, or face a chaotic, multi-million-dollar disaster later. An affordable manual pentest has a huge return on investment. It's about preventing the fire instead of fighting it.
Why Can’t I Just Use an Automated Scanner?
Automated scanners only find common, known problems. They can't think like a person or find unique flaws in your systems. Real attackers are creative, and our human pentesters copy their methods. Our OSCP, CEH, and CREST certified experts find the critical issues scanners always miss.
How Does Penetration Testing Help with Compliance?
Many regulations like SOC 2, PCI DSS, and HIPAA require regular penetration testing. A pentest provides proof to auditors that your security is working. Traditional firms are slow and expensive, making this a challenge. We provide the same quality report auditors need, but we do it affordably and deliver it in under a week.
How Quickly Can I Get a Pentest Report?
This is where we are different. Traditional firms can take weeks or months. We know you can't wait that long. Our process is built for speed. We deliver a complete, actionable pentest report to you in under one week. Your team can start fixing problems right away.
Don't let the high cost of a data breach become your problem. At Affordable Pentesting, we deliver fast, expert, and affordable security testing to protect your business. Get a clear view of your weaknesses and take control of your security.
Get a no-nonsense quote from our team today.
.svg)
