Data security is the lock on your door, and compliance is the building code you have to follow. You need both. Getting a SOC 2 or HIPAA certification depends on proving your security actually works. Most businesses get stuck here, facing slow timelines and crazy prices from traditional penetration testing firms. We fix that with affordable pentesting that starts in 24 hours.
Understand Your Security and Compliance Needs

Too many businesses treat data security and compliance like two separate chores. That's a huge mistake. They are two sides of the same coin, and a solid security posture is what powers any real compliance program. Without it, you are just creating paperwork that won't help you during a real security incident or a tough audit.
A compliance framework like SOC 2 or HIPAA asks you to prove you have the right security controls in place. You can’t just say you have them; you have to show they work. That is where practical security testing, like an affordable penetration test, comes in. An urgent penetration testing engagement can quickly give you the evidence you need.
A strong security foundation is built on practical, verifiable actions that protect your data. This includes basic things like access controls, encryption, and firewalls. These are the exact technical defenses auditors look for. When you invest in them, you are directly investing in your ability to pass that compliance audit and show you are not just checking a box.
Every security measure you put in place creates the evidence you need for compliance. Having a clear security policy is the bridge that connects your technical actions to your compliance goals. If you need a starting point, our information security policy template can help. Strong data security and compliance builds trust with customers and protects your business.
The High Cost of a Security Mistake

Ignoring data security and compliance is an expensive gamble. A single security incident can create a financial black hole that many businesses never escape. The price tag goes way beyond fixing a technical bug. When you have a security failure, it kicks off a chain reaction of costly consequences that hit your budget hard.
The moment a breach occurs, the meter starts running. You are immediately on the hook for incident response teams, forensic investigators, and legal fees. Then, add the crippling fines from regulators for non-compliance. These penalties are designed to hurt, often running into millions for serious violations of frameworks like GDPR or HIPAA.
A security incident is a full-blown business crisis. The costs multiply quickly, starting with forensic teams and ending with years of rebuilding lost customer trust. The average cost of a data breach has soared to a staggering $4.44 million globally. You can learn more about these rising financial impacts from BrightDefense.
The initial shock is bad enough, but the long-term damage is where the real pain is. A tarnished reputation is incredibly difficult and expensive to fix. Customers simply do not want to do business with companies they cannot trust with their data. When you stack these catastrophic expenses against the cost of being proactive, the choice is clear. A traditional pentesting firm might charge $25,000 to $50,000 for a single engagement. In contrast, our affordable penetration testing services deliver the same critical insights, with prices starting at just $2,000 for manual testing and $500 for automated scans.
Quickly Decode Major Compliance Frameworks
Trying to handle data security and compliance can feel like drowning in acronyms like SOC 2, HIPAA, and ISO 27001. Figuring out which ones matter to your business is the first step. The complexity is a real headache for companies. A solid 69% of businesses report that getting compliant takes anywhere from three months to over a year. You can see more hard numbers in Vanta's latest compliance report.
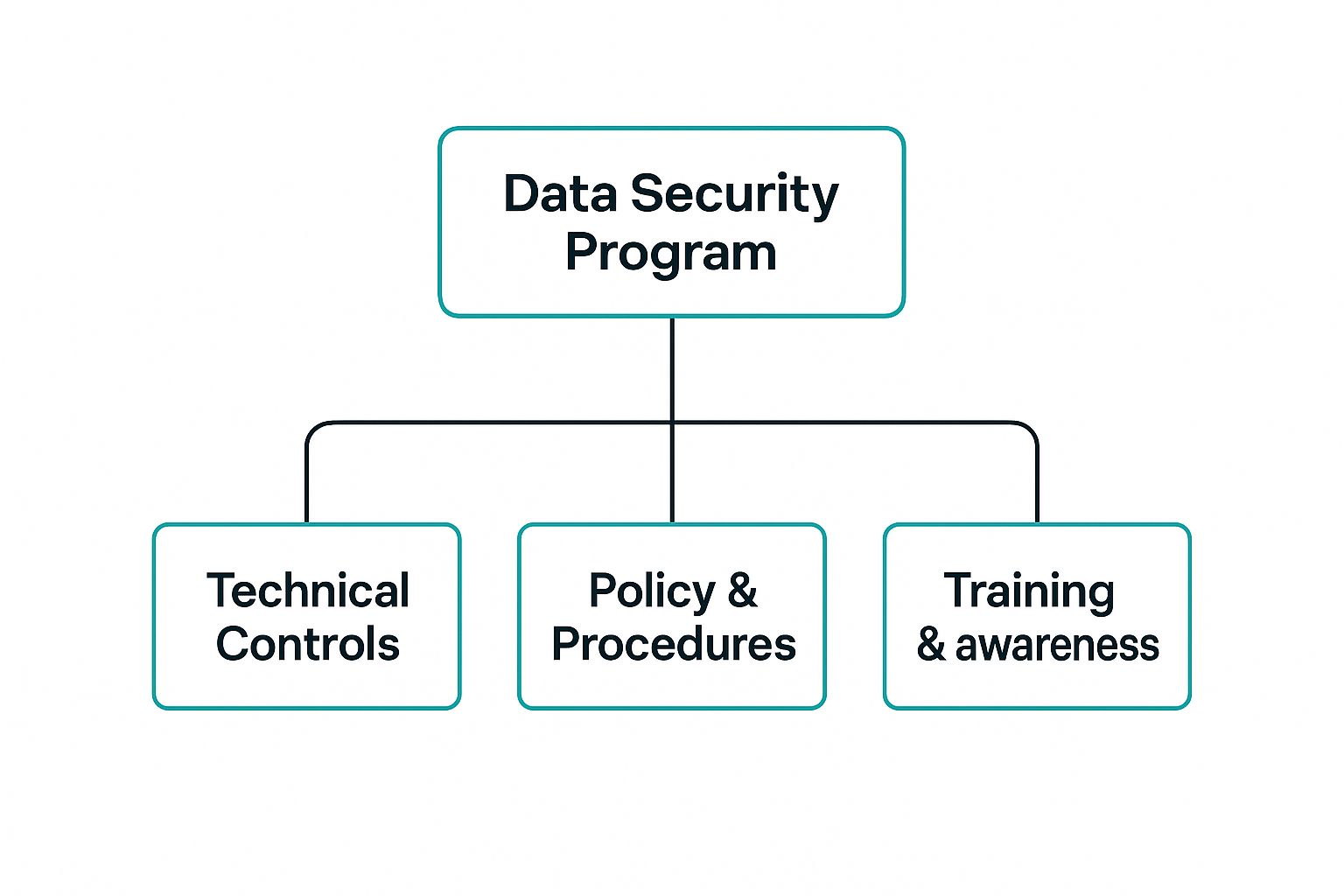
To cut through the noise, you need a clear, focused data security program. A successful program is not just about technology. It is about balancing your tools with solid processes and, most importantly, your people. When all three work together, you are in a much better position to protect your data and get your SOC 2 penetration testing done right.
Here is a quick look at the most common compliance frameworks you will run into. If your company handles customer data, especially in the cloud, SOC 2 is for you. Passing a SOC 2 audit tells customers you have strong, verified controls to keep their data safe, which is why it is non-negotiable for most SaaS companies and requires a pentest.
HIPAA is the law for protecting sensitive patient health information in the U.S. If your organization handles protected health information (PHI), you must be HIPAA compliant. This applies to insurance companies, billing services, and any business associates like a SaaS platform that handle PHI. PCI DSS is for any business that takes credit cards. It is a set of rules to fight credit card fraud, and compliance is mandatory. ISO 27001 is the international gold standard for managing information security, providing a complete blueprint for building a security program. Ultimately, all of these frameworks demand a deep understanding of your own security posture, which is why affordable penetration testing is so valuable. To learn more about structuring this process, check out our guide on building a cybersecurity risk management framework.
Pentesting is Your Compliance Secret Weapon

Compliance is not about having a dusty binder full of policies. It is about proving your security actually works. This is where a penetration test becomes your most valuable tool, turning your data security and compliance program from theory into proven reality. A pentest is a controlled, ethical cyberattack where our certified hackers (OSCP, CEH, CREST) try to break into your systems just like a real attacker would.
A pentest report is undeniable evidence that you are actively managing your security risks. For frameworks like SOC 2, HIPAA, and ISO 27001, regular security testing is often a requirement. Handing over a clean, third-party pentest report is one of the fastest ways to satisfy auditors and prove you have done your due diligence. It makes the entire audit process smoother.
It is always better to find your own security problems than to have an auditor find them for you. A penetration test gives you a clear, prioritized list of vulnerabilities to fix. This proactive approach is the cornerstone of strong data security and compliance. In fact, a solid pentest report can become a powerful sales tool, showing clients you take their data security seriously.
The old way of doing this was painfully slow and expensive. Traditional firms often quote $25,000 to $50,000 for a single pentest and can take weeks to start. That model is broken. We saw this problem and built a better way. You do not need to spend a fortune to get a high-quality, audit-ready penetration test. Our entire approach is built for speed and value, delivering the same level of expertise without the ridiculous price tag. Our fast penetration testing services are designed to get you the proof you need for your audit, fast. For a deeper look, check out our guide on penetration testing best practices.
Stay Ahead of New Security Threats
The rules of data security and compliance are always changing because the threats are changing every day. The security strategy that protected you last year might be useless against the attacks being cooked up right now. If you want to stay compliant, you have to stay ahead of what is coming next. Emerging technologies, especially generative AI, are giving attackers a brand-new playbook.
The speed of change is a massive challenge. The 2025 Thales Data Threat Report shows that 69% of organizations see the rapid evolution of technology as their biggest security risk from Generative AI. A worrying 24% of companies still have little to no confidence they even know where all their sensitive data is stored. That is a fundamental failure of data security and compliance. If you do not know where your data is, you cannot protect it.
An effective security program is not about buying every new tool. It is about building a flexible and resilient foundation. This means staying informed about major trends, using adaptable security tools, and creating a security-aware culture through regular, practical training. Your compliance efforts are only as good as your ability to defend against current threats.
This is where regular, affordable penetration testing becomes a core part of your strategy. It gives you a real-world look at how your defenses hold up against the attack techniques being used today. By continuously testing and adapting, you ensure your data security and compliance efforts stay relevant and effective. This proactive stance keeps you protected from emerging threats and ready for any auditor.
Your Action Plan for Security and Compliance
Knowing you need solid data security and compliance is one thing; actually building it is another. Let's walk through a straightforward, practical roadmap to turn that knowledge into a real security program that protects your business and satisfies auditors. This is about taking logical steps to manage your risk in the real world.
First, start with a risk assessment. You have to know what you are defending against. Figure out what data matters most, what the most likely threats are, and where you are currently weak. This process gives you a clear, personalized picture of your risk profile so you can focus your time and money where it will have the biggest impact.
Next, choose the right compliance frameworks that actually apply to your business. If you are a SaaS company, SOC 2 is likely your top priority. If you handle patient data, it is all about HIPAA. Pick the one or two frameworks that are non-negotiable for your industry and customers. This keeps your compliance efforts from spiraling out of control.
Then, implement core security controls. This is the hands-on part. Based on your risks and chosen frameworks, put essential security measures in place like strong access controls, encryption, and a locked-down network configuration. These are the technical foundations of any good data security and compliance program. Finally, schedule regular pentesting to prove your controls actually work. An affordable penetration test is the single most effective way to validate all your hard work. Traditional firms love to quote $25,000 for a test with a six-week waiting list. We can get your affordable penetration testing started in 24-48 hours and deliver your report in just five days.
Your Top Security and Compliance Questions
Let's cut through the noise and tackle the most common questions we hear about data security and compliance. A vulnerability scan is automated, like a robot checking for unlocked doors. A penetration test, or pentest, is a manual, human-driven attack simulation where a certified ethical hacker actively tries to break into your systems. This is why serious audits like SOC 2 require a pentest.
For most major compliance frameworks, the baseline for a pentest is at least once a year. For SOC 2, an annual penetration test is the minimum. PCI DSS is stricter, mandating annual external and internal pentests, plus more after any significant changes. HIPAA requires ongoing risk analysis, for which a pentest has become the gold standard. Annual pentesting is your starting point.
So many founders believe enterprise-grade security has to come with a staggering price tag. Traditional firms reinforce this by quoting $25,000 to $50,000 for a single pentest. The good news is you do not need that kind of budget. You can achieve rock-solid data security and compliance by being smart. An affordable penetration test delivers the exact same critical insights and audit-ready reports without the inflated cost. Our penetration testing services start at just $2,000 for a manual pentest.
Ready to prove your security without the enterprise price tag? At Affordable Pentesting, we deliver high-quality, audit-ready penetration tests fast. Get started today by visiting us at https://www.affordablepentesting.com to secure your free consultation.
.svg)
.jpg)