Implementing zero trust security starts with a simple idea: the old way of protecting your business is broken. Your team works from everywhere and your data is in the cloud, so the idea of a secure office network is gone. This means you need a new rule: never trust, always verify.
Your Old Security Model Is Failing

For years, security was like building a castle. You had strong walls like firewalls and VPNs to keep bad guys out. Anyone inside was trusted.
But your company doesn't work that way anymore. Your data is in cloud apps like Microsoft 365 or AWS. Your employees connect from home, coffee shops, and airports. This pokes huge holes in your old castle walls.
Remote work is now standard, but VPNs can be a problem. If an employee's laptop gets hacked, an attacker can use the VPN to get right inside your network. Your office firewall can't see what's happening in the cloud, leaving that data exposed. The old model also assumes anyone inside is trustworthy, but a single stolen password can lead to disaster.
This is why the Zero Trust market is growing so fast, expected to hit $86.57 billion by 2030. Businesses are forced to adapt because the old way no longer works. You can discover more about the market's rapid growth to see why everyone is switching. Assuming anything inside your network is safe is a costly mistake.
Understand The Core Zero Trust Principles
Zero Trust isn't a piece of software you install. It's a different way of thinking about security. The main idea is simple: trust nothing, verify everything. If you are new to this concept, you can learn more about What is Zero Trust Security and why it matters.
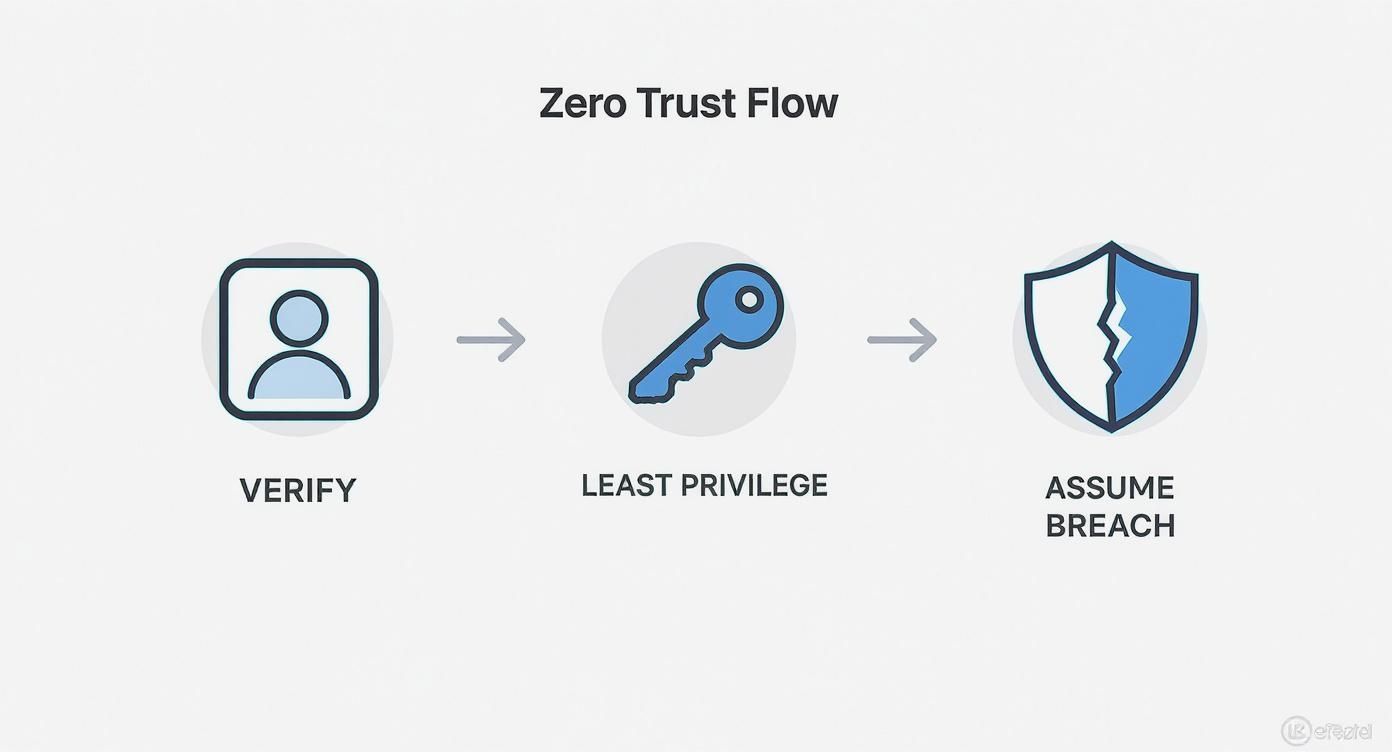
This whole approach is built on three simple ideas. First is to verify explicitly. This means every single request to access your data is checked. Every time. It doesn't matter who it is, they get checked.
Second is least privileged access. This means you only give people the bare minimum access they need to do their job. Nothing more. If your marketing person only needs two apps, they shouldn't be able to touch anything else. This shrinks the area an attacker can damage if they get in.
Finally, you must assume a breach. You build your security assuming a hacker is already inside your network. This forces you to create defenses that can trap and stop a threat. You do this by breaking your network into tiny, isolated zones, a technique called micro-segmentation. If one area is breached, you can seal it off from the rest.
Your Practical Roadmap To Zero Trust Security
Starting with Zero Trust doesn't have to be overwhelming or expensive. You don't need to rip everything out and start over. The key is to start small and focus on protecting what matters most.
This infographic shows the core idea: always verify, grant minimum access, and assume a breach is possible.
First, you need to define your protect surface. This is your most important data, applications, and assets. Think about your customer lists, financial records, or secret source code. Focusing on these crown jewels makes the project much more manageable.
Next, map how your data moves. Who needs to access it? What apps connect to it? This shows you exactly where to put up your security gates. It gives you a clear picture of who should and shouldn't have access to your critical assets.
With a clear map, you can build your Zero Trust architecture. The foundation is strong identity verification. This means using multi-factor authentication (MFA) is a must for everyone. It's one of the most effective security steps you can take.
Finally, segment your network. This means breaking your network into small, isolated zones. If an attacker gets into one zone, they are trapped there and can't move to other parts of your system. For more details on this process, check out a comprehensive guide to implementing Zero Trust Security.
Choosing Affordable Tools For Zero Trust
You don't need a huge budget for Zero Trust. You probably already have some of the tools you need, and many others are affordable. The goal is to make smart choices that secure your business without costing a fortune.
Your Zero Trust plan starts with identity. Before you can approve or deny access, you have to know who is asking. This is handled by Identity and Access Management (IAM) tools.
Many businesses already use powerful IAM solutions like Microsoft Entra ID or Okta. These are a great starting point. Your first step should be to turn on multi-factor authentication (MFA) for everyone. This one change makes it much harder for attackers to use stolen passwords.
After you secure identities, you need to protect the devices people use. This doesn't mean buying expensive hardware. Endpoint Detection and Response (EDR) software can watch employee laptops for suspicious activity and stop attacks automatically. Network micro-segmentation can be done with software to divide your network into small zones, trapping any intruders.
Recent data shows that 81% of businesses have started using Zero Trust, and you can discover more insights about the state of Zero Trust adoption. Your strategy should be to build on what you already have. You can also explore our guide on leveraging security testing automation tools to get more from your budget.
Validate Your Security With Affordable Pentesting

You've set up your Zero Trust rules and tools. But how do you know if it actually works? A security policy on paper is one thing, but a defense that stops a real hacker is another. This is where penetration testing, or pentesting, is essential.
It's easy to make a small mistake when setting up complex security rules. One wrong setting can create a giant security hole. A pentest is like a fire drill for your security. It's a controlled attack to find weak spots before real attackers do. Without this real-world test, you are just hoping your security works.
We know traditional pentesting is slow, expensive, and often gives you reports that aren't helpful. We created our service to fix this problem for startups and small businesses who need fast, real results.
Here’s how we're the affordable alternative. We deliver your full report within one week, so you can start fixing things immediately. We offer high-quality manual pentesting at a price that fits your budget. Our testers are certified experts with qualifications like OSCP, CEH, and CREST. They think like hackers to find flaws that automated tools miss. You can learn more about our process by reading what is penetration testing.
A successful pentest proves your Zero Trust strategy is working. It gives you real confidence in your security. It's also proof for auditors, investors, and customers that you are serious about protecting the business. Don’t just assume your security works. Let us help you prove it.
Your Top Questions About Zero Trust Answered
Starting a new security plan always leads to questions. IT managers, CISOs, and startup founders often worry about the same things: the cost, the impact on employees, and how it works with their current tools. Let's get straight to the answers.
First, people worry if Zero Trust will annoy their employees with constant logins. A well-designed system should actually be smoother. Modern tools are smart and use context. An employee logging in from their usual device and location is low-risk and might not see any extra steps. But a login from a new country at 3 AM will trigger more checks.
Next is the cost. You don't need to buy one giant, expensive platform. You likely already have key tools like Microsoft Entra ID or Okta. The strategy is to build on what you have and add affordable tools where needed. Zero Trust is a framework, not a single product.
You can absolutely keep using your existing tools. Zero Trust is about adding security controls around the apps and infrastructure you already have. You can protect old and new systems without a massive migration project.
Finally, how do you know if it's all working? The only way to be sure is with regular, manual penetration testing. A pentest simulates a real attack to see if your defenses hold up. Traditional pentesting is too slow and expensive for most businesses, which is why we offer an affordable alternative. We deliver actionable reports within one week. Our OSCP, CEH, and CREST certified pentesters find the critical flaws that scanners miss, giving you real confidence in your security.
Don't just assume your security controls are effective—prove it. Affordable Pentesting provides fast, manual, and affordable penetration tests to validate your defenses and meet compliance needs. Get your report in one week. Find out how we can help by visiting us at https://www.affordablepentesting.com.
.svg)
