SQL injection is a major threat that can lead to a data breach, but finding and fixing these flaws doesn't have to be slow or expensive. Traditional pentesting firms are costly and take months, but our certified experts deliver a clear, actionable report in about a week. We offer an affordable way to secure your application and meet compliance needs.
Why SQL Injection Is Still a Major Problem
SQL injection is a simple trick attackers use to steal your data. They sneak malicious commands into places like a login form or a search bar. If your application isn't built to stop them, your database runs these commands, handing over sensitive information.
This happens when your application takes what a user types and puts it directly into a database query. Without proper defenses, attackers can rewrite your queries to bypass security. This lets them grab customer data, financial records, or internal secrets. You can learn more in our guide on what an SQL injection attack is.
The Scale of the SQL Injection Threat
This isn't a small problem. The 2025 Edgescan Vulnerability Statistics Report found that SQL injection was the top critical vulnerability, making up 19.52% of all serious findings. Even though it's an old attack, companies keep making the same basic mistakes. You can see the findings in the full report.
SQL injection is always on the OWASP Top 10 list of the most critical security risks. For IT managers and CISOs, a single SQL injection flaw can cause a major data breach, leading to huge fines and lost customer trust. This is a business problem, not just a tech problem.
How to Stop SQL Injection with Secure Code
The best way to stop SQL injection is by writing secure code from the start. If your application's foundation is weak, you'll always be playing defense. Strong coding habits close the door on attackers before they even get a chance.
This means building security into your development process. It’s not about expensive tools, it’s about simple, secure habits that stop common attacks. This flowchart shows how easily user input can turn into a full-blown data breach.
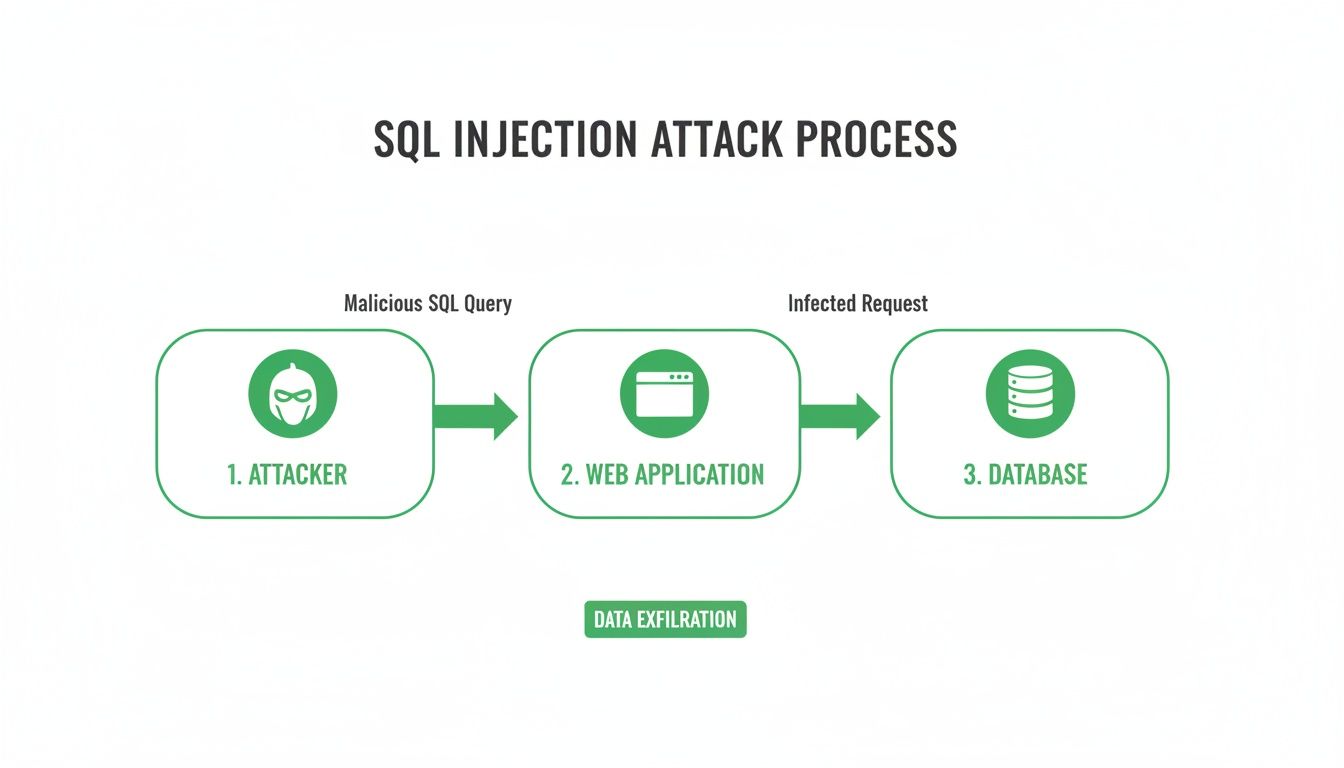
The diagram shows the application is the weak spot where an attacker’s malicious input is passed right to the database.
Always Use Parameterized Queries to Stop Attacks
If you only do one thing, do this. The best way to stop SQL injection is by using parameterized queries, also called prepared statements. Think of it like this: your SQL command and the user's input are sent to the database in two separate, locked boxes. The database knows one box is instructions and the other is just data, so it never mixes them up.
Because the database engine treats the input as simple text, any malicious commands an attacker tries to inject are harmless. It’s the best practice for a reason. Making this a rule for your developers is the biggest security win you can get. Our guide to security code reviews can help CISOs and IT managers check if this is being done right.
How to Block Attacks with Input Validation
Even with secure code, you need extra layers of defense. Input validation and escaping are like having a bouncer check everyone who comes through the door. They work together to make sure nothing malicious ever reaches your database. This is your critical second line of defense.

Input validation means checking what a user sends to your server and rejecting anything that looks wrong. If you ask for a phone number, the input should only have numbers. Anything else, like a piece of a SQL command, gets thrown out immediately. This simple step stops a huge number of automated attacks.
Why You Must Implement Strict Input Validation
The first rule of security is to never trust user input. Input validation is how you enforce this rule. It stops attacks and also improves your data quality by preventing weird errors in your application.
Be as specific as possible. Don't just check if an input is text, check that it matches the exact format you expect. This is called safelisting, where you only allow known good data formats. It's much better than trying to block bad inputs because attackers always find new ways to hide their code.
For any IT manager or founder, making sure your team validates all input is a must. Without it, you are leaving the door wide open for attackers. That’s why an affordable manual penetration test is so important. Our OSCP and CEH certified pentesters find the issues your team may have missed, with a clear report in about a week. Fill out our contact form to learn more.
How to Strengthen Your Database Security
Even with perfect code, a poorly configured database can leave you vulnerable. This is where we harden the infrastructure itself. Think of it as layered defense. If an attacker gets past your code, a secure environment will limit the damage they can do.
For CISOs and IT managers, these controls are what security in depth is all about. This is also what auditors for frameworks like ISO 27001 look for. They want to see multiple layers protecting your sensitive data.

Why to Enforce the Principle of Least Privilege
If you remember one thing from this section, make it this: the principle of least privilege. It’s simple. Your application's database account should only have the bare minimum permissions it needs to work. Nothing more.
If your app only needs to read and write customer data, it shouldn't be able to change tables or create new users. By limiting what the account can do, you contain the damage from a successful SQL injection. An attacker who compromises the application is stuck with the same limited permissions.
How to Harden Your Server Configuration
Beyond user accounts, your database server configuration is critical. Default settings are often made for ease of use, not security. You need to actively turn off things you don’t need. Start by disabling unnecessary database features.
For instance, some database systems have functions that can run operating system commands. If your app doesn't need this, turn it off. Also, make sure error messages are generic. Detailed errors can give an attacker a map to your database structure. For more on protecting your online assets, see these essential website security best practices. To dive deeper, check out our guide on database security best practices.
Find Hidden Flaws with Affordable Pentesting
You’ve followed secure coding guides and hardened your servers, but you might still wonder what you missed. A penetration test, or pentest, is like hiring a certified ethical hacker to try and break into your application. They use the same tactics a real attacker would.
The goal is to find complex vulnerabilities that automated scanners miss. You need a human expert to spot flaws that require creativity. Our team holds top certifications like OSCP, CEH, and CREST, so you get real, battle-tested expertise.
Why Automated Scanners Are Not Enough
Automated tools are great for finding simple problems, but they can't understand context. They won't spot a complex, multi-step attack that an experienced human tester can uncover in minutes. A pentester can link small issues together to create a huge security hole.
For any company that needs to meet compliance standards like SOC 2, PCI DSS, or HIPAA, a manual pentest is often a requirement. Auditors want to see that you've had a real expert validate your security, not just run a basic scan. These vulnerability trends and their impact show why this is so important.
Making Critical Security Testing Affordable
We know why many startups and small businesses skip this step. Traditional pentesting firms are slow and expensive. They charge huge rates, take months to deliver a report, and sometimes find very little. We built our service to fix that broken model.
Our approach is both affordable and fast. We believe every company deserves access to high-quality security testing without breaking their budget. We have a streamlined process that delivers a comprehensive report in about a week, not months.
What a Manual Penetration Test Finds
Our ethical hackers go far beyond what any automated tool can do. They actively probe your application to find vulnerabilities that scanners can't, such as business logic flaws, complex injection attacks, and authentication bypasses. After you've secured your code, a manual pentest is the final, crucial step to validate your defenses.
Don't wait for a real attacker to test your security. Contact us through our form to see how our fast, affordable pentesting can help you find and fix hidden flaws before they become a real problem.
Your SQL Injection Questions Answered Here
We’ve covered the main ways to stop SQL injection, but a few questions always come up. Getting straight answers is key for IT managers, founders, and compliance officers trying to build a smart security plan. Let’s tackle some of the most common ones.
Is a Firewall Enough to Stop SQL Injection?
A Web Application Firewall (WAF) is a great layer of defense, but it's not a complete solution. Think of a WAF like a fence around your building. It’s good at stopping known troublemakers by filtering traffic based on common attack patterns. It’s an important first line of defense.
But a skilled attacker can often find clever ways to disguise their malicious queries to get past the WAF. Relying only on a WAF creates a false sense of security. The best strategy is to use a WAF as one part of a layered defense, combined with secure coding and regular pentesting to fix flaws at the source.
How Often Should We Get a Penetration Test?
The honest answer is it depends. If you need to meet a compliance standard like PCI DSS, an annual pentest is usually the minimum. It’s a box you have to check.
But for strong security, we recommend a pentest after any major change to your application, like a new feature launch. For high-risk apps handling sensitive data, testing twice a year is a smart investment. Our affordable and fast model makes this achievable without draining your budget.
My Developers Use an ORM Is That Enough?
Using an Object-Relational Mapping (ORM) framework greatly lowers your risk of SQL injection, but it does not make you invincible. Most ORMs generate parameterized queries by default, which is the best way to prevent these attacks. They do a great job.
The danger comes when developers face a complex database task that the ORM doesn’t handle easily. They might be tempted to bypass the ORM and write a raw SQL query by hand. If that raw query is not perfectly parameterized, it can create the same SQL injection flaws you thought you had eliminated. A penetration test is the best way to verify that your ORM's security is working and no vulnerable raw queries have slipped through.
Don't leave your application's security to chance. At Affordable Pentesting, we provide fast, thorough, and budget-friendly penetration testing to help you meet compliance and protect your data. Our certified experts deliver actionable reports in about a week. Get in touch to secure your business today at https://www.affordablepentesting.com.
.svg)
