Your network is the backbone of your business, but attackers are constantly trying to break in. Spotting a real threat in a sea of data is impossible without the right tools. Choosing the best network security monitoring tools is a critical decision that impacts your ability to prevent data breaches and protect customer information.
This guide cuts through the marketing fluff. We will look at top network security monitoring platforms, from big names like Splunk to specialized tools like Darktrace. We will cover key features, pros, cons, and pricing to help you evaluate your options.
But monitoring tools only show you what’s happening. How do you know if your defenses will stop a real attacker? That's where validation comes in. At Affordable Penetration Testing, we offer fast penetration testing designed to find the holes your tools might miss. We help you meet compliance requirements like SOC 2 and ISO 27001 with actionable reports, often in just 72 hours. We test your defenses so you can be confident they work.
Understanding SIEM and NDR Tools
Splunk is a leading Security Information and Event Management (SIEM) platform. It pulls in data from almost any source across your network, like logs and events. This makes it a powerful tool for detecting and responding to complex threats in real-time.
For companies getting ready for audits like SOC 2, Splunk is a huge help. It provides the centralized logging needed to meet SOC 2 penetration testing requirements. The platform is great at connecting different events to spot advanced attack patterns that might otherwise be missed.
- Best For: Large companies with dedicated security teams and complex environments.
- Pricing Model: Splunk's pricing is based on how much data you send it each day. This can get expensive as you grow.
- Implementation: Splunk is powerful but complex. Setting it up right often requires a specialized expert.
Pros:
- Highly flexible with thousands of apps and add-ons
- Powerful search language for deep investigations
- Large community and lots of support resources
Cons:
- High costs for licenses and the servers to run it
- Requires special skills to manage effectively
Website: https://www.splunk.com/en_us/products/enterprise-security.html
Choosing Open Source Security Platforms
Elastic Security combines SIEM and Extended Detection and Response (XDR) in one open platform. It collects a wide range of data, giving you a single view for finding and stopping threats. This makes Elastic a flexible choice for teams who want control without high costs.
Its open design means you can add custom data sources and write your own detection rules. This is a great alternative to more rigid, closed systems. For SOC 2 pentesting, Elastic provides the necessary log analysis to prove your security controls are working, without the huge price tag tied to data volume.

- Best For: Businesses on a budget and security teams with technical skills who want a customizable platform.
- Pricing Model: Elastic's pricing is based on the server resources you use, not how much data you send. This is often cheaper.
- Implementation: Getting started is easier with pre-built integrations, but getting the most out of it requires hands-on tuning.
Pros:
- Clear and often more affordable pricing model
- A powerful free version with lots of features
- Strong community and tons of integrations
Cons:
- Requires more manual work to get it enterprise-ready
- Lacks some of the built-in automation of competitors
Website: https://www.elastic.co/security/siem
Integrating with Your Existing Network
Cisco Secure Network Analytics provides network visibility without installing agents on every device. It turns your existing network gear into a grid of sensors. This gives your security team a full view of all traffic, helping to spot insider threats and malware.
If your company already uses a lot of Cisco products, this tool is a natural choice. It provides valuable data for incident response and helps with compliance reporting for standards like PCI DSS and HIPAA. Its ability to analyze encrypted traffic without decrypting it is a major plus for privacy.
- Best For: Companies with a lot of Cisco gear or those needing an agentless network detection solution.
- Pricing Model: Pricing is complex and usually based on traffic volume. You'll need a custom quote.
- Implementation: Setup can be complicated and requires careful planning to make sure it performs well.
Pros:
- Works seamlessly with other Cisco security products
- Can be deployed on hardware, as a virtual machine, or in the cloud
- Gives visibility into encrypted traffic without decryption
Cons:
- Licensing can be confusing and expensive
- Focuses on network data, so you might need other tools for logs
Website: https://www.cisco.com/c/en/us/products/security/secure-network-analytics.html
Meeting Strict Compliance Requirements
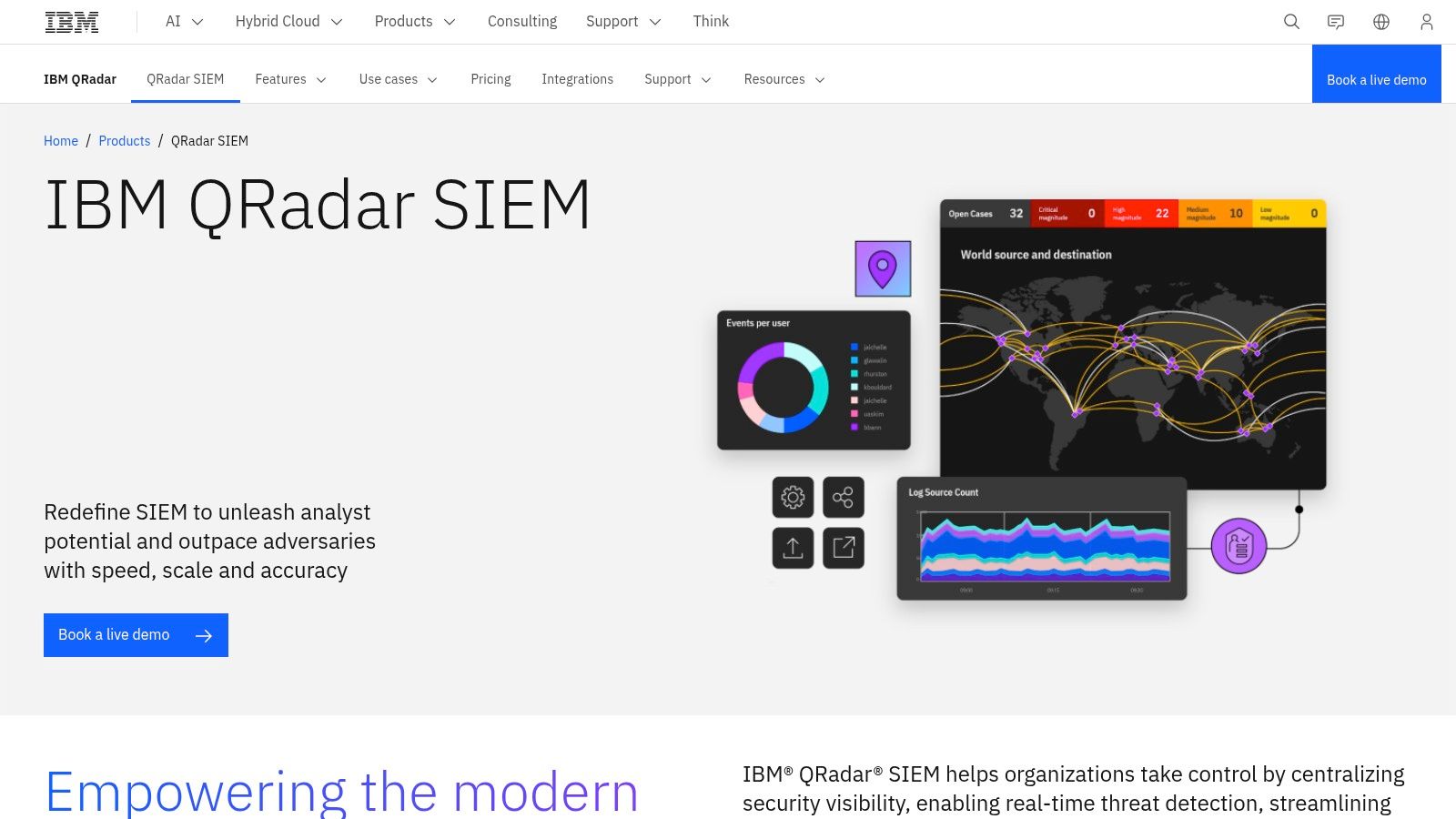
IBM QRadar SIEM is a security analytics platform popular in regulated industries like finance and healthcare. It collects log data and network flows from your entire environment. This makes it a great tool for connecting the dots between related activities to find and prioritize real threats.
For businesses dealing with tough compliance rules, QRadar is a solid choice. Its detailed reports and clear audit trails are exactly what you need for SOC 2 penetration testing. It helps you prove you are continuously monitoring your network and are ready to respond to incidents.
- Best For: Companies in regulated industries that need strong compliance and analytics features.
- Pricing Model: Pricing is typically based on events per second (EPS) and flows per minute (FPM). A free community edition is available.
- Implementation: It has over 700 pre-built integrations, but you need to tune the rules to reduce false alarms.
Pros:
- Excellent features for compliance reporting and audits
- Scales well in large, complex environments
- Huge library of integrations and apps
Cons:
- Requires a lot of tuning to work well
- Can be complex to manage without a dedicated expert
Website: https://www.ibm.com/products/qradar-siem
Monitoring for Cloud Native Environments
Datadog Cloud SIEM brings security monitoring to its popular observability platform. It is built for modern, cloud-based companies. It analyzes logs, metrics, and traces from your entire tech stack, connecting performance data with security alerts.
This integrated approach helps teams find threats faster by providing full context in one place. For businesses needing SOC 2 pentesting, Datadog's logging and pre-built detection rules help meet evidence requirements. It’s designed for the scale and speed of the cloud.

- Best For: Cloud-focused companies and DevOps teams who already use Datadog for monitoring.
- Pricing Model: You pay based on the volume of log data you send. Costs can add up quickly if you're not careful.
- Implementation: Known for being fast and easy to set up. You can get meaningful security data in hours, not weeks.
Pros:
- Combines security with logs and metrics for better context
- Quick to set up with over 700 built-in detection rules
- Great for cloud and serverless environments
Cons:
- Can get expensive if you have a lot of log data
- May not be the best fit for companies with mostly on-premise servers
Website: https://www.datadoghq.com/product/security-monitoring
Finding Compromised User Accounts
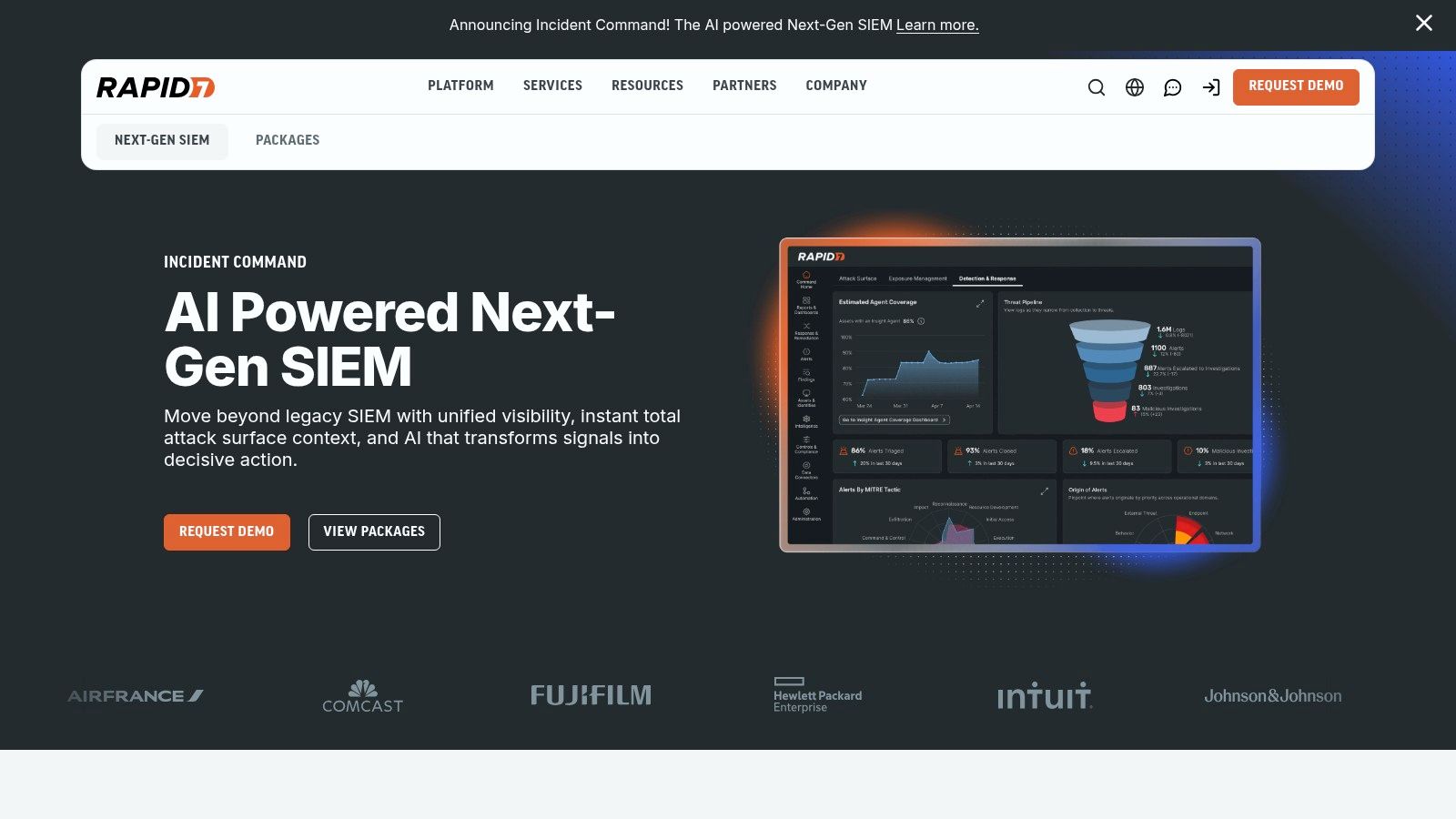
Rapid7 InsightIDR is a cloud SIEM that makes threat detection and response simpler. It combines user behavior analytics, endpoint detection, and log management in one place. This makes it very effective at spotting compromised user accounts and attackers moving through your network.
InsightIDR speeds up investigations by putting events from endpoints, logs, and cloud services into a single timeline. This helps security teams understand the full story of an attack without having to piece everything together manually.
- Best For: Mid-sized to large companies that want a user-friendly, cloud-based SIEM with strong detection features.
- Pricing Model: Pricing is usually based on the number of devices you monitor, not data volume, which makes costs more predictable.
- Implementation: As a cloud solution, setup is fast. But you need to fine-tune it to manage costs and reduce false alarms.
Pros:
- Fast cloud deployment and an easy-to-use interface
- Clear workflows that guide security analysts
- Strong options for managed detection and response (MDR) services
Cons:
- You need to carefully manage data sources to control costs
- Custom reports can be less flexible than some other tools
Website: https://www.rapid7.com/products/insightidr
Using AI to Find Hidden Threats
The Vectra AI Platform is a leading Network Detection and Response (NDR) solution. It uses AI to find threats across cloud and on-premise environments. It focuses on attacker behaviors instead of just signatures, helping to catch sophisticated attackers who have already bypassed your first line of defense.
Vectra's AI models are trained to think like attackers. This helps reduce alert noise by focusing on high-priority threats that pose a real risk. This is critical for finding new threats and insider risks that other tools might miss.
- Best For: Medium to large companies with complex environments looking for high-quality, automated threat detection.
- Pricing Model: Vectra’s pricing is for enterprises and requires a custom quote.
- Implementation: Can be deployed as a physical or virtual device. Success requires careful planning to ensure you have visibility everywhere.
Pros:
- Strong AI that reduces false positives
- Covers network, identity, and cloud threats
- Automatically prioritizes threats to save time
Cons:
- Pricing is geared towards larger companies
- No public pricing information is available
Website: https://www.vectra.ai
Automatically Stopping Threats in Real Time
Darktrace works differently from many other tools. It uses self-learning AI to understand what "normal" looks like for your network. Instead of relying on pre-written rules, it builds a dynamic understanding of every user and device. This lets it spot tiny changes that indicate an emerging threat.
This AI-driven approach is great for meeting tough compliance needs like SOC 2. By providing constant visibility and detecting unusual activity, Darktrace shows you have a proactive security posture. It can even stop threats automatically, containing attacks in seconds without disrupting your business.
- Best For: Companies of all sizes that want AI-driven detection and automated response, especially those with smaller security teams.
- Pricing Model: Darktrace uses a subscription model. Pricing depends on factors like the number of devices and network size.
- Implementation: Setup is usually simple as the system learns passively. Fine-tuning the automatic response takes some time.
Pros:
- Detects new and advanced threats that rule-based tools miss
- Autonomous response stops threats 24/7
- Excellent visibility across complex IT and cloud environments
Cons:
- The "black box" nature of its AI can make it hard to explain alerts
- Can create false alarms while it's first learning your network
Website: https://www.darktrace.com/products/network
Getting Deep Network Forensic Capabilities
ExtraHop RevealX is a Network Detection and Response (NDR) platform that works without agents. It gives you deep visibility by analyzing network traffic. It combines decrypted traffic analysis and packet-level forensics into one solution. This makes it great for finding threats moving sideways across your network.
For security teams securing complex environments, RevealX offers a huge advantage. It can decrypt modern TLS 1.3 traffic and understands over 90 protocols. This gives analysts a clear view into encrypted communications where threats often hide.
- Best For: Companies that need deep visibility into encrypted traffic and strong network forensic capabilities.
- Pricing Model: ExtraHop pricing is customized and requires a quote. It is available directly or through marketplaces like AWS.
- Implementation: Deployment involves sending traffic to the RevealX sensor. Setting up decryption can be complex.
Pros:
- Strong forensic capabilities with long-term packet capture
- Combines multiple network security functions in one tool
- Powerful decryption features for modern traffic
Cons:
- Implementing decryption requires careful architectural planning
- Can be a premium-priced solution
Website: https://www.extrahop.com
Building Your Own Powerful Monitoring Solution
Security Onion is a free and open-source platform for threat hunting and security monitoring. It bundles a suite of the best open-source tools like Zeek and Suricata. While the software is free, Security Onion Solutions offers commercial support, training, and hardware to help you run it effectively.
This makes it one of the most cost-effective and powerful network security monitoring tools available. It's great for teams who want to build strong internal skills without the high license fees of commercial tools. It simplifies collecting and correlating different types of security data.
- Best For: Organizations with skilled security or IT teams who want a powerful, low-cost solution and are comfortable with Linux.
- Pricing Model: The software is free. You can pay for optional professional support, hardware, and training.
- Implementation: Requires solid Linux and networking skills to manage long-term.
Pros:
- Extremely low-cost software with a big, active community
- Provides comprehensive visibility by combining multiple data types
- Great for training your team in security monitoring and threat hunting
Cons:
- Requires significant technical expertise to operate
- Commercial support is an added cost but often necessary
Website: https://securityonionsolutions.com
Getting Foundational Network Visibility
Zeek is an open-source network security monitor that works differently from traditional tools. Instead of just using signatures, Zeek watches network traffic and creates detailed logs of everything it sees. These logs provide a rich dataset for deep forensic analysis and threat hunting.
For security teams who need to know exactly what happened on their network, Zeek's data is priceless. The detailed logs for DNS, HTTP, and other protocols offer solid evidence for incident response and compliance. It is all about creating a long-term, searchable record of network activity.

- Best For: Organizations with skilled security teams who want deep network visibility and a customizable framework.
- Pricing Model: Zeek is completely free. Your only costs are the hardware to run it and the experts to manage it.
- Implementation: Requires ongoing tuning and integration with other tools like a SIEM for log storage and analysis.
Pros:
- Generates incredibly detailed and useful network logs
- Highly customizable through its own scripting language
- Completely free with a large, active community
Cons:
- Doesn't have a built-in user interface or dashboard
- Requires significant expertise to manage and interpret
- No official commercial support
Website: https://zeek.org
Finding Security Tools in the Cloud
AWS Marketplace is a digital catalog where you can find, buy, and deploy third-party software in AWS. For security teams, it’s a one-stop shop for a huge range of network security monitoring tools, including leading SIEMs and NDRs. It's an essential resource for building out your security in the cloud.
The platform makes buying software much easier by adding the charges to your existing AWS bill. This is helpful for teams who need to quickly test different tools or meet an urgent penetration testing need for compliance. Instead of long contract negotiations, you can subscribe to a tool with a few clicks.

- Best For: Companies heavily using AWS who need to quickly buy and deploy security monitoring solutions.
- Pricing Model: Varies by vendor. Options include free trials, subscriptions, and custom offers. Billing is handled through your AWS account.
- Implementation: Varies by product. Many tools offer templates to make deployment faster and easier.
Pros:
- Greatly simplifies buying software and consolidates billing
- Makes it easy to run fast trials and proofs-of-concept
- Tight integration with native AWS services
Cons:
- Quality and support can vary widely between vendors
- Many top-tier tools still require you to contact the seller for pricing
Website: https://aws.amazon.com/marketplace/solutions/security/threat-detection
Tools Are Only Half The Battle
Choosing the right network security monitoring tools is a big step. But just installing a new tool isn't enough. A shiny new dashboard full of alerts doesn't mean you're secure. Misconfigurations and gaps in your coverage can leave you exposed, even with the best tool.
The most important question to ask is, "How do I know this is actually working?" This is where affordable penetration testing comes in. A pentest simulates a real-world attack to see how your defenses hold up. It's the ultimate reality check for your security tools and your team.
A skilled penetration tester will try to get past your firewalls and evade your alerts. The final report gives you a clear, actionable roadmap to fix the gaps and strengthen your security. It’s the difference between hoping you are secure and proving you are.
Many businesses think penetration testing is too expensive. Traditional firms often quote high prices and take weeks to start. This makes compliance testing for frameworks like SOC 2 penetration testing seem out of reach. We started our company to solve this exact problem.
We provide fast, high-quality, and affordable penetration testing from certified experts (OSCP, CEH, CREST). Whether you need an ASAP pentest for a client or a security audit for compliance, we deliver comprehensive reports quickly. Our pricing starts at just $4,999.
Don't assume your tools are catching everything. Validate your defenses with a real-world test. Get a quote from our contact form and prove your security works.
.svg)
