A pen test service is like hiring a professional, ethical hacker to try and break into your systems. The goal is to find security holes before a real attacker does. This isn't just an automated scan; it's a manual process where our certified experts think creatively, just like a real hacker.

What Exactly Is A Pen Test Service?
You've likely heard the terms pen test, penetration testing, and pen testing. They all mean the same thing: a simulated cyberattack on your systems to find vulnerabilities an attacker could exploit. It’s all about protecting customer data and building trust.
Instead of just running a program that looks for known issues, a real penetration test relies on human intelligence. Our experts, holding certifications like OSCP, CEH, and CREST, actively try to exploit your defenses. This hands-on approach finds complex flaws that automated tools always miss.
Why Your Business Needs Penetration Testing
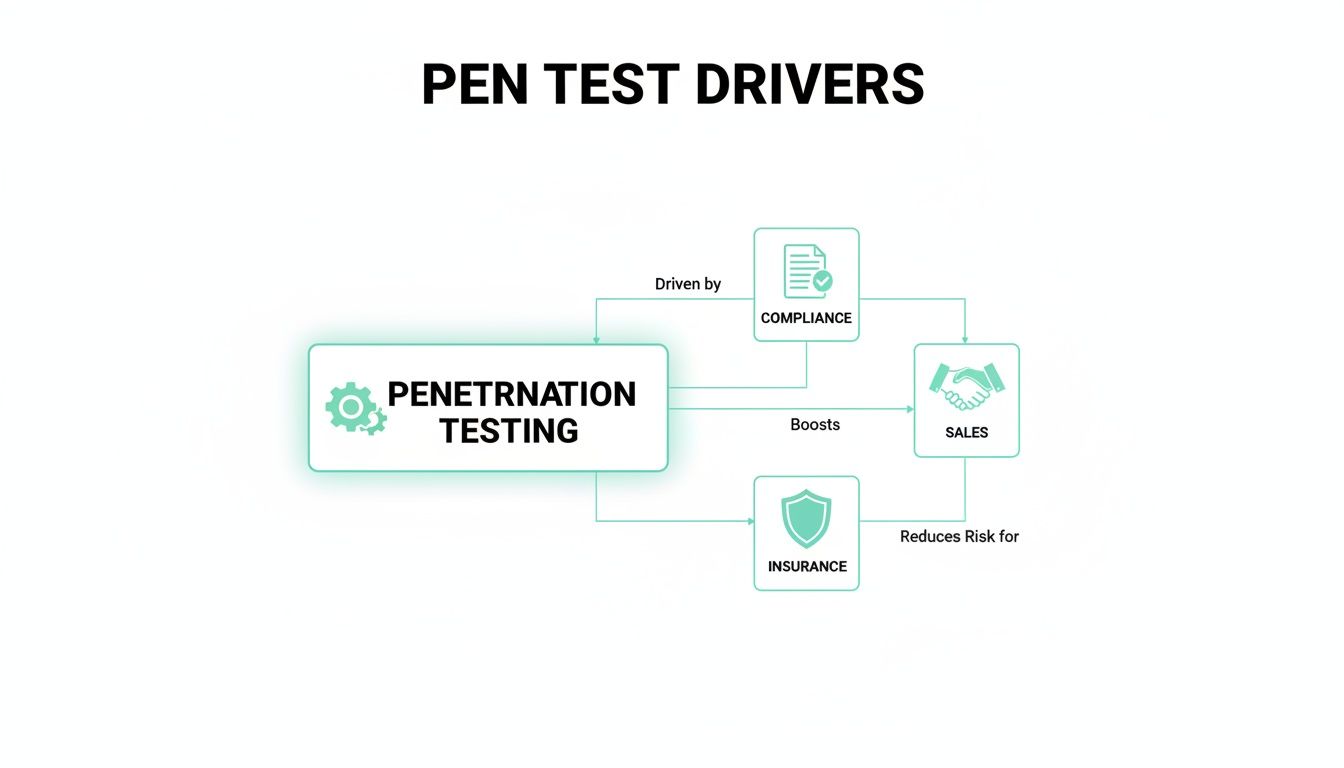
Compliance is a huge reason businesses need a pen test. Frameworks like SOC 2, PCI DSS, HIPAA, and ISO 27001 often require an annual penetration test. Failing to comply can lead to big fines and lost trust with your customers.
But a pen test service is more than a compliance checkbox; it’s a powerful sales tool. When you're trying to land bigger clients, they want proof your security is solid. A clean pentest report is hard evidence you're serious about protecting their data.
Understanding Different Types Of Pen Tests
Not all penetration tests are the same. Choosing the right one ensures you find the vulnerabilities that actually matter to your business. Think of it like a home inspection: you need the right specialist for the job.
Let's break down the common types of penetration testing so you can choose wisely. A properly scoped pen test service gives you the insights you need without wasting time or money. Each test is designed for a specific part of your technology stack.
External And Internal Network Pen Tests
An external network pen test is like checking the locks on the outside of your building. Our ethical hackers look at your systems from the internet, just like a real attacker. They search for weaknesses in your firewalls and servers visible to the public.
An internal network pen test simulates an attacker who is already inside. This could be a disgruntled employee or someone who got in through a phishing email. We see how much damage they could do once they have a foothold.
Web App And Mobile App Pen Tests
If your business relies on a web or mobile app, this is the most critical pen test service for you. An application penetration test focuses on flaws in your software's code and logic. This is where automated scanners fail because they can't understand business context.
Our testers manually probe your app for critical vulnerabilities like those in the OWASP Top 10. These are the flaws that let hackers steal customer data directly from your platform. You can learn more in our guide on the different types of penetration testing.
Affordable API And Cloud Pen Tests
APIs are the connectors that pass data between your services. An API pen test targets these connections to ensure they can't be tricked into leaking data. When creating a secure API, testing is how you prove your security works.
A cloud penetration test focuses on your AWS, Azure, or GCP environment. It hunts for common misconfigurations, which are the leading cause of cloud breaches. Our certified experts check permissions and settings to ensure your cloud is locked down.
How We Deliver Fast And Affordable Pentests
When you need a pentest, you need it fast and on budget. Traditional security firms take weeks or months to deliver a report while charging huge prices. That model is broken for growing businesses.
We built our pen test service to be different. We focus on speed, affordability, and the high-quality manual testing that auditors and customers demand. You get a full report within one week.

Certified Experts Performing Manual Pen Testing
The core of our service is manual penetration testing. Our team is made up of certified experts holding top industry credentials like OSCP, CEH, and CREST. These certifications prove our team has the advanced skills to perform a thorough security assessment.
You're not just getting an automated scan. You're getting a dedicated, certified human expert who thinks like an attacker. This is exactly what auditors for SOC 2, HIPAA, and PCI DSS want to see in a pen test report.
Reports With Clear Actionable Steps
A report full of confusing jargon is useless. Our final report is designed to be understood by everyone, from your leadership to your engineers. It starts with a clear Executive Summary that explains business risk in plain English.
The second part is a Detailed Technical Breakdown. For every vulnerability, we provide step-by-step instructions on how to replicate and fix the issue. Our pen testing service even includes free retesting to confirm your fixes worked.
How To Choose The Right Pen Test Partner
Picking a penetration testing partner is a big decision. You need a team that delivers real value, not just a long report. Look for a partner who is certified, transparent, and helps you fix what they find.
The wrong partner will waste your budget and leave you with a useless report. A great partner becomes an extension of your team, providing the clarity you need to strengthen your defenses.
Why Certifications And Manual Testing Matter
First, look for certifications like OSCP, CEH, and CREST. They are proof that a tester has the skills and ethical standards to perform a high-quality pen test service. These credentials show a real-world understanding of how to find security flaws.
Next, make sure they focus on manual testing. An automated scan is not a penetration test. A real penetration test involves a certified expert using their brain and experience to act like a real attacker.
How To Prepare For Your Penetration Test
Getting ready for a pen test is straightforward. A little prep work helps our testers get started quickly, which means we can deliver your report in about a week. We're here to work with you, not against you.
The first step is defining the scope. You tell us exactly which systems or applications you want us to test. This keeps the pen test service focused on your most important assets.
Your Top Pen Testing Questions Answered
Have questions about penetration testing? We have direct answers.
How Long Does A Pentest Take?
For most projects, like a web app or network test, we deliver your complete report in one business week. Our process is lean and focused, so you get results fast without waiting for weeks.
Is A Scan The Same As A Pentest?
No, and your auditor knows the difference. An automated scan is a tool that finds common, known mistakes. A manual penetration test uses a certified human expert to find complex business logic flaws that scanners always miss.
What Kind Of Report Will I Get?
You get a report built for action. It has an Executive Summary for leadership that explains business risk in plain English. The Technical Details section gives your engineers clear, step-by-step instructions to fix every finding.
Why Are Your Pentests So Affordable?
We cut out the bloat. Big security firms charge for their massive overhead and sales teams. We don't have that. You pay for one thing: expert security work from certified professionals at a price that works for your budget.
Ready for a fast, affordable, and compliance-ready penetration test? Contact us through our website for a quote and get your report in just one week.
.svg)
