Most pentest reports are a total waste of time. They're often bloated, 100-page documents choked with jargon that your engineers can't use and your executive team won't read. At Affordable Penetration Testing, we deliver clear, actionable reports in days, so you can fix what matters and pass your compliance audits fast.
Why Traditional Pentest Reports Fail You

There’s a huge problem with old school penetration testing services. They spend most of their time writing reports that are designed to look impressive, not to be useful. This slow and expensive process is why so many companies dread their annual security audit.
The result? You get a document that ticks a box for your auditor but creates a headache for everyone else. Your developers are left struggling to find clear instructions, and your leadership has no way to quickly grasp the actual business risk. It’s a mess that burns your team's time and your company's money.
Understand Old School Versus Modern Reporting
The core issue is that old reports are written for other pentesters, not for the people who actually need to fix the problems. They are almost always filled with excessive jargon, a lack of prioritization, and vague remediation steps that leave your engineers guessing what to do next.
A well structured report saves your team countless hours by focusing on the vulnerabilities that genuinely threaten your business. This is why a solid pentest report template is so crucial. It enforces the consistency and clarity that auditors for SOC 2, HIPAA, and ISO 27001 want to see.
Get Actionable Reports With Core Components

So what separates a useful pentest report from a digital doorstop? It all comes down to clarity and action. Traditional firms often spend up to 60% of their testing time just writing the report, padding it with fluff to justify their high prices. We think that is backward. The value is not in the page count; it is in how quickly and easily your team can fix the real problems.
A great report needs an executive summary that a non technical leader can read in under three minutes to understand the company's security posture. It also needs detailed findings that developers can actually use, with reproducible steps and proof of concept. Finally, it must provide a practical, prioritized remediation plan based on real business risk.
Structure Your Report For Compliance Audits

When you need an ASAP pentest for a compliance audit like SOC 2 penetration testing, the report is your primary piece of evidence. A great report makes the audit go smoothly. A bad one gets you stuck in a nightmare of back and forth questions from your auditor, which is the last thing you need when a big deal is on the line.
The structure is everything. An auditor needs proof, not a long story. They are looking for a clear line connecting the test you performed to the specific controls in the framework. Anything less just creates more work for them and a massive headache for you. This is why our OSCP, CEH, and CREST certified pentesters build reports specifically for compliance needs.
Align Your Report With Auditor Needs
Think of your auditor as a very busy person with a checklist. Your report’s job is to help them tick every box without having to hunt for information. That means the structure needs to be logical and directly tied to what they actually care about: your methodology, scope, and proof of remediation.
For example, a SOC 2 pentesting report absolutely must document the testing methodology clearly. It also needs to define the scope with surgical precision, listing every single asset, IP address, and application that was tested. Any ambiguity here is an immediate red flag for an auditor. We ensure every report is built to pass the first time.
Turn Security Findings Into Developer Tasks
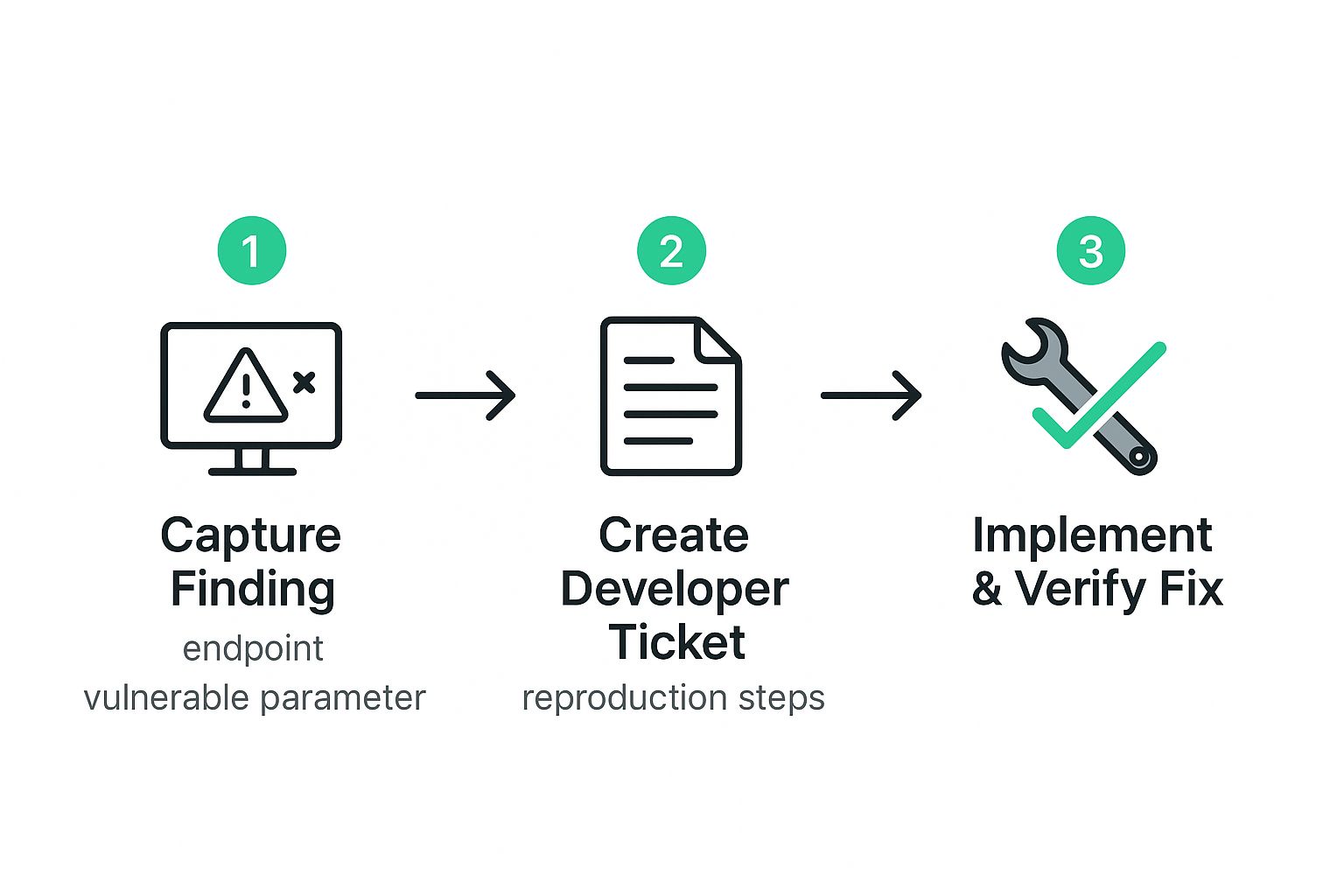
A pentest report is completely worthless if your developers cannot act on it. This is where expensive, old school security firms fail. They write for other pentesters, not the engineers building your product. A great report bridges that gap, translating a security finding directly into a developer ticket.
The whole point is to make remediation fast and frictionless. That means no vague advice. Your team needs a recipe they can follow to replicate the issue, understand its impact, and ship a fix without a dozen follow up emails. This is how we provide fast penetration testing that actually improves your security posture. For MSPs looking to provide this value to their clients, we offer the same affordable pricing and reporting through programs like MSP pentesting.
Create Developer Tickets That Actually Work
A developer ticket from a pentest finding has to be a self contained unit of work. It needs to provide the exact endpoint, the vulnerable code snippet or parameter, and a simple command to replicate the problem. Anything less just creates more work for your engineers.
This level of detail means a developer can validate the finding in minutes and start working on a patch immediately. It respects their time and gets the vulnerability patched faster, which is the entire reason you get affordable penetration testing in the first place. This process also improves overall development practices, which you can read more about in our guide on security code reviews.
Manage Remediation And Retesting The Right Way
Finding vulnerabilities is only half the battle. The real goal, especially for compliance, is proving you have fixed them. A solid pentest report template is the start of a clear workflow: find, fix, and verify. Many traditional firms turn this crucial verification step into another invoice. They deliver a report, you fix everything, and then you have to pay them again to confirm the fixes.
We do not believe in charging extra for re-testing. It is a fundamental part of a complete penetration test, not an optional add on. Once your developers push the fixes, we get right back to work to validate them. This is all included in our flat penetration testing pricing, saving you time and money and helping you get a clean report for your auditor faster.
Common Questions About Pentest Reports
We get a lot of the same questions from IT managers, CISOs, and startup founders. They all need reliable security testing, but they do not have a massive budget. Here are some straight answers about pentest reports and our approach to affordable penetration testing services.
How Much Should A Pentest Report Cost?
This is a huge source of frustration. Traditional security firms bundle report writing into a massive project fee, anywhere from $15,000 to $100,000. A good chunk of that is just for their bloated, slow reporting process. We think that is insane.
Our affordable penetration testing services have a flat starting price of $4,999. That price includes a clear, actionable report and free re testing to verify your fixes. No hidden fees, no confusing invoices, just a straightforward security audit.
What Should Be In A Good Pentest Report?
A useful report is a practical tool that helps your team fix things fast. A solid pentest report template always has an executive summary for leaders, a clear scope and methodology for auditors, prioritized findings based on business impact, and actionable remediation steps for developers. It should make your auditor’s job easy by providing a clear trail from risk to resolution.
This is exactly what you need to meet SOC 2 penetration testing requirements. While manual testing is essential for this deep dive, it's also worth exploring how automated penetration testing can help you maintain continuous compliance.
How Long Does It Take To Get The Report?
Old school firms can take weeks, sometimes even a month, to deliver your report. When you have an urgent compliance deadline or a customer demanding proof of security, that slow timeline is a deal killer. We move much faster. Because our entire process is built for efficiency, you get actionable findings within days of the test's completion, not weeks. This speed is a game changer for any team needing an urgent penetration testing solution.
Vulnerability Assessment Versus A Pentest Report?
This one trips a lot of people up. A vulnerability assessment is usually just an automated scan that spits out a long list of potential weaknesses. It is noisy and full of false positives. A penetration test report is the result of a hands on, manual security audit by a certified professional. An expert validates findings, throws out false positives, and shows how a real attacker could exploit the issues. This is the level of detail required for SOC 2 pentesting and other major compliance frameworks.
Ready for a pentest report that your team can actually use? At Affordable Penetration Testing, we deliver clear, actionable reports in days, not weeks, with free re-testing included. Get your free quote today.
.svg)
