Trying to figure out vulnerability assessment vs penetration testing? Let's cut the jargon. A vulnerability assessment is an automated scan that lists potential security weaknesses. A penetration test is a manual, human-led attack that proves if those weaknesses can actually be exploited to cause real damage. If you need to pass a SOC 2 audit, you need a real pentest. At Affordable Penetration Testing, we deliver auditor-ready reports in days, not months.
Defining the Core Differences
A lot of companies get stuck here, burning time and money on the wrong security test. While both are designed to find security flaws, they serve completely different purposes. One is about finding what could be wrong, while the other proves what is wrong.
A vulnerability assessment is broad and automated. Think of it as a spell-checker for your security. It runs your systems against a huge database of known issues and generates a report. It's fast, relatively cheap, and a great habit for regular security checks. The downside? It’s notorious for false positives and doesn’t tell you which of the hundred findings actually pose a real threat.
A penetration test, or pentest, is a targeted, manual process. Our certified ethical hackers (OSCP, CEH, CREST) think like a real attacker. They don’t just find a vulnerability; they actively try to exploit it to see how deep they can get. This is exactly what auditors for SOC 2, HIPAA, and ISO 27001 need to see—proof your defenses can stand up to an attack. While traditional firms charge a fortune, our affordable penetration testing services start at just $4,999.
This infographic lays out the difference between the two approaches at a glance.
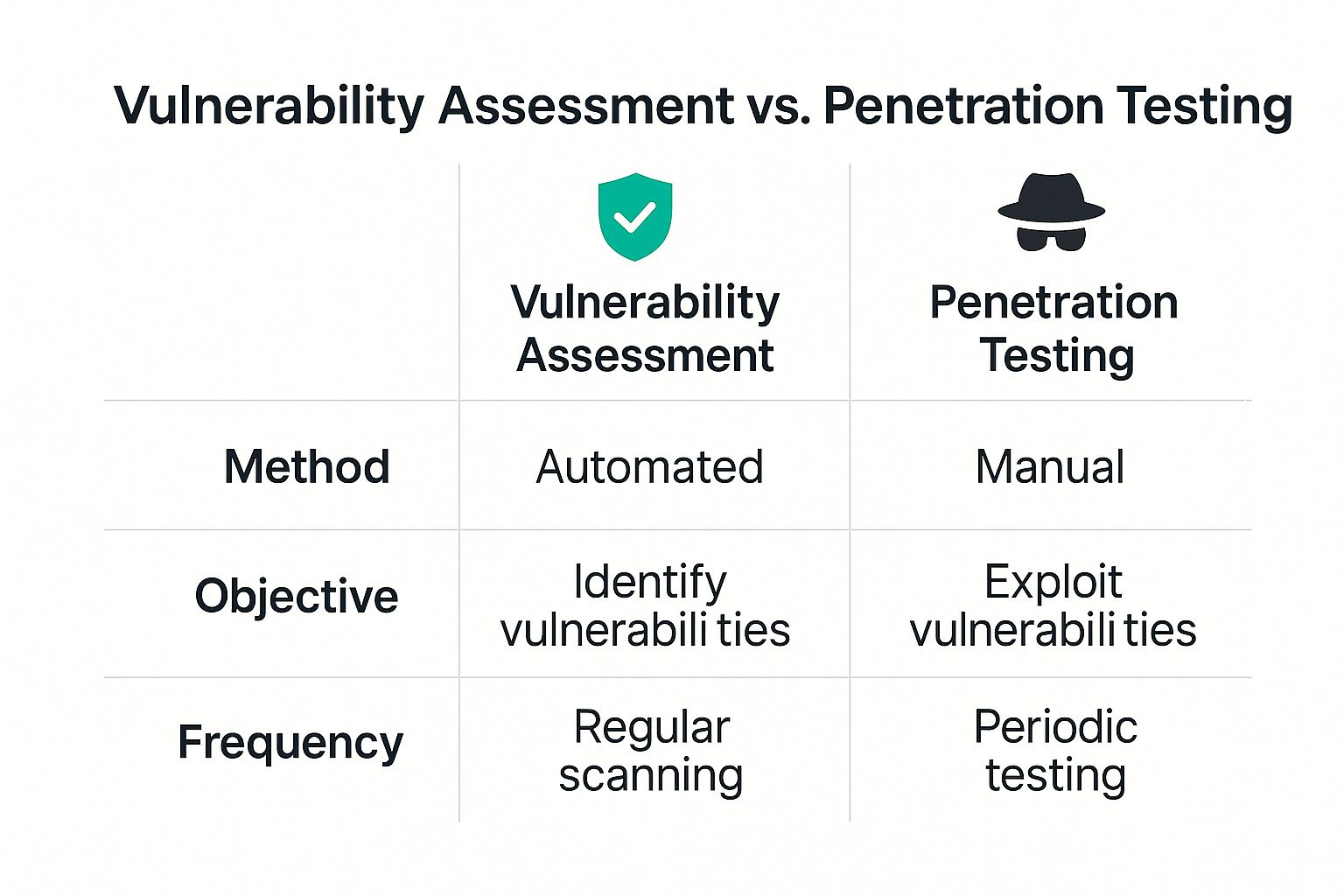
As you can see, the real split is between automation versus manual expertise. One is about identifying potential flaws, the other is about actively exploiting them.
Vulnerability assessments and penetration testing diverge significantly in their scope and depth. Assessments are great for scanning for known issues with automated tools, which makes them cost-effective for frequent checks. In contrast, penetration testing services simulate real-world cyberattacks where skilled hackers try to break in, giving you a true measure of impact. With traditional firms, this can cost anywhere from $4,000 to over $100,000. You can discover more insights about the roles these tests play on wiz.io.
Quick Comparison of Assessment vs Pentest
To make it even clearer, here’s a side-by-side summary. Use this table to quickly see the key differences and figure out which security test fits your immediate compliance and security goals.
Ultimately, a vulnerability assessment gives you a checklist of things to investigate. A penetration test gives you a clear, prioritized list of real security gaps that an attacker could use against you tomorrow.
Understanding What Vulnerability Assessments Do
Think of a vulnerability assessment as casting a wide, automated net to see what you can catch. It’s a security scan that uses software to check your systems against a massive, constantly updated database of known security flaws. We're talking things like outdated software versions or common server misconfigurations.
The whole point is to generate a comprehensive list of potential weaknesses across your network and applications. Because the process is automated, it’s fast and pretty inexpensive. This makes it a fantastic choice for routine, ongoing security check-ups to maintain good cyber hygiene.

The end result of a vulnerability assessment is a report, usually a very long one. It lists every single potential issue the scanner found, typically ranked by a generic severity score. In short, it tells you what might be wrong. But that's where its value ends. The report doesn't confirm if these vulnerabilities are actually exploitable in your specific environment. It won't tell you the real-world business impact, leaving your IT team with a massive to-do list but no clear idea of where to start. This is not enough for a SOC 2 penetration testing requirement.
The assessment just identifies potential problems; it never tries to exploit them. That long list of findings can be overwhelming, which is why having a clear strategy for dealing with it is so important. You can dig deeper by exploring some vulnerability management best practices to see how to handle the output effectively. Ultimately, a scan is just the first step. A penetration test is the definitive final word on your security.
How Our Affordable Penetration Testing Works
So, what exactly is an affordable penetration test? Think of it as a focused, human-driven simulation of a real cyberattack. This isn't just another automated scan that spits out a long list of potential problems. Our certified ethical hackers actively try to exploit the very vulnerabilities a scan might find.
This process gives you concrete proof of exploitability, which is a non-negotiable requirement for compliance audits like SOC 2 penetration testing. We've stripped away the high costs and slow timelines of traditional firms to give you what you actually need: clear, actionable reports that help you fix what matters and pass your audits. We even offer an ASAP pentest for urgent needs.

The difference between a scan and a true pentest is the human expert. Our affordable penetration testing services are led by certified professionals with credentials like OSCP, CEH, and CREST. They think like real attackers, creatively chaining together small weaknesses, something software just can't do. Our entire process is built for speed, designed to get you from quote to final report fast.
Here’s how we deliver real value without the outrageous penetration testing pricing of legacy firms:
- Scoping and Planning: We start with a quick call to define the test's goals. Are you focused on network penetration testing, application security testing, or meeting specific SOC 2 pentesting requirements? We tailor the scope to your exact needs.
- Information Gathering: Just like a real adversary, our testers gather intelligence on your systems. This initial reconnaissance is crucial for identifying potential entry points and attack vectors.
- Exploitation: This is where the magic happens. Our ethical hackers manually attempt to bypass your security controls and exploit the vulnerabilities they've found. We don’t just report a weakness; we prove its impact.
- Reporting and Remediation: You get a straightforward report that prioritizes findings based on real-world risk. We provide clear, simple steps to fix the issues, empowering your team to get to work immediately.
The output of our fast penetration testing is far more than a list of flaws. It’s a practical roadmap for strengthening your security and a golden ticket for your compliance audits. Auditors for frameworks like SOC 2, HIPAA, and ISO 27001 need to see that you’ve properly validated your security controls against a realistic attack. Our penetration test report is designed to be auditor-ready.
Comparing Automated Scans vs Human Expertise
The biggest difference in the vulnerability assessment vs. penetration testing debate boils down to the methodology. One relies on automated tools, while the other brings in critical human expertise. This is where you separate a simple checklist from a true, real-world security validation.
A vulnerability assessment is a systematic, automated process. It uses software to scan your network and applications, checking what it finds against massive libraries of known issues. The whole point is broad coverage and speed; it spits out a list of potential weaknesses, fast.
Automated scans are predictable but have significant limitations. They are notorious for high false positives, creating noise and wasting your team's time. They have no business context and are blind to complex flaws like business logic errors. If you want to dig deeper into the limits of automation, check out our guide on automated penetration testing.
This is where a real pentest delivers its value. Our affordable penetration testing services combine powerful automated tools with the creative, critical thinking of our OSCP, CEH, and CREST certified experts. A human tester doesn't just find a vulnerability; they think like an attacker to actually exploit it. An automated scan can tell you a door is unlocked. A penetration tester will open that door, walk through the building, and see if they can reach the vault. Our experts mimic real-world attacker tactics, providing definitive proof of exploitability that auditors demand.
Meeting Compliance Demands Like SOC 2 and ISO
When an auditor asks for security testing, they aren't looking for a list of potential problems. Compliance frameworks like SOC 2, ISO 27001, and HIPAA require you to prove your security controls actually work. This is where the debate over a vulnerability assessment vs penetration testing gets settled, especially when an audit is on the line.
A vulnerability scan is a great starting point for internal housekeeping, but it almost never satisfies an auditor on its own. They need to see that you’ve tested your defenses against a realistic, simulated attack. And for that, a penetration test is non-negotiable. An affordable penetration testing report, however, delivers the independent, expert validation they're looking for. It shows you’ve moved beyond basic scanning and have actively tried to break your own systems.
Here's what compliance frameworks demand:
- SOC 2 Penetration Testing: For a SOC 2 audit, a pentest is often an explicit requirement. Auditors need to see you've found and fixed exploitable vulnerabilities to prove your security program isn't just theory.
- ISO 27001: This standard is all about implementing controls based on a thorough risk assessment. A penetration test provides critical, real-world data for that process.
- HIPAA: The Security Rule requires covered entities to perform an "accurate and thorough" risk analysis. A pentest is a best practice for meeting this requirement, as it demonstrates a serious effort to protect patient health information from attackers.
A vulnerability scan can be part of your overall security strategy, but it’s the penetration testing services that deliver the concrete proof needed for a successful audit. We have a detailed guide that explores more penetration testing best practices. Our fast penetration testing is built to meet these compliance needs head-on, delivering the documentation you need quickly. Don't let a compliance deadline sneak up on you.
Why You Need Fast and Affordable Pentesting
Let’s be honest: the old-school penetration testing model is broken. It’s painfully slow, shockingly expensive, and usually ends with a phonebook-sized report so technical it’s almost useless. Growing businesses on a tight deadline for SOC 2 or ISO 27001 simply can't afford to wait weeks for a quote and then months for the actual test.
This outdated approach forces a dangerous choice. Companies either shell out a fortune or they skip it, crossing their fingers that a simple vulnerability scan is good enough. Spoiler: it isn’t. We built our affordable penetration testing services to fix this exact problem, making high-quality, essential security testing accessible to everyone.
Traditional penetration testing pricing can easily hit tens of thousands of dollars. It’s not uncommon to wait four to six weeks just to get on a tester's schedule. You shouldn't have to choose between your budget and your security. We believe every business deserves access to certified, expert-led penetration testing without the enterprise price tag. Our model delivers exactly that.
We provide fast penetration testing with transparent pentest pricing starting at just $4,999. You get a clear quote in hours and can kick off your test in days, not months. Our reports are built for action, giving you the clear, auditor-ready documentation you need to nail your SOC 2 audit. Don't let high costs and sluggish timelines block you from real security and compliance.
We Have Answers To Your Questions
It's easy to get tangled up in the jargon. Vulnerability assessment vs. penetration testing? It can feel confusing, but the distinction is actually pretty straightforward. Here are some of the most common questions we hear, broken down into simple terms.
For most compliance frameworks like SOC 2, HIPAA, and ISO 27001, you need a pentest once a year. Think of it as your annual security physical. You should also get a pentest done anytime you make a major change to your applications or network.
Is a vulnerability scan enough for my SOC 2 audit? Almost never. A vulnerability scan is like a spell-check for your security. Auditors for frameworks like SOC 2 need to see that your security controls can stand up to a real person trying to break in. That requires a manual, expert-led SOC 2 penetration test.
Why are other pentests so expensive? You’ve seen the quotes. Traditional security firms are saddled with massive overhead and clunky manual processes. We cut out the bloat to deliver high-quality, affordable penetration testing without the enterprise price tag. Our pentest pricing starts at just $4,999 because we believe real security shouldn't be a luxury.
Help! My audit is next week. Can you do an urgent penetration testing? Yes. This is what we do. We specialize in fast penetration testing for teams staring down a tight deadline. Big firms can take weeks just to get a scoping call on the calendar. We can often kick off a test within a few days and get you the auditor-ready report you need.
Ready to secure your systems and sail through your next audit without breaking the bank? We deliver fast, certified, and auditor-ready penetration tests designed for businesses like yours.
Get a no-nonsense quote today by filling out our contact form.
https://www.affordablepentesting.com
.svg)
.jpg)