Are you frustrated with overpriced and slow penetration tests? External vulnerability scanning is a great first step, but it only shows you potential problems, not what's actually exploitable. We combine automated scanning with fast, affordable manual pentests to give you a clear, actionable report in about a week.
Find What an External Vulnerability Scan Misses

Think of a scan like a security guard quickly checking for unlocked doors from the sidewalk. It’s an automated tool that finds obvious, known security issues on your website and servers. This gives you a quick snapshot of your security.
But a scan only tells you what might be weak. It can't tell you if a hacker could actually get in. That's where our certified pentesters come in.
Our automated scans check for deviations from essential website security best practices. We also identify many common web application security vulnerabilities.
This scan gives our OSCP and CEH certified pentesters a starting point. They then manually confirm what’s truly a risk and deliver an affordable, easy-to-read report in about a week.
See How External Vulnerability Scanning Works
So what happens during a scan? It's like a robot checking every digital door your company has facing the internet. The scanner sends signals to your public systems to see what it can find.
These checks look for open ports and identify the software you're running. The tool then compares this information against a huge list of known vulnerabilities. It quickly shows what an attacker sees from the outside.
Most scans are unauthenticated, meaning the tool acts like a stranger with no logins. This is great for spotting easy targets. While scans are a good start, it is important to understand the different automated penetration testing tools and their limits.
We use this process to map your network before our certified pentesters (OSCP, CEH, CREST) find what’s really exploitable. This approach gets you a fast, affordable report in about one week.
Learn Vulnerability Scanning vs Penetration Testing
This is where many businesses get confused and waste money. An external vulnerability scan is an automated checklist. It flags potential problems based on things it already knows.
A penetration test is a certified human trying to break in like a real attacker. They think creatively to find weaknesses a scanner can't.
Think of it this way: a scan says a window might be unlocked. A pentest confirms a burglar can climb through it and steal your stuff. It's the difference between a guess and proof.
This quick decision tree shows how we begin to assess your public-facing digital assets.
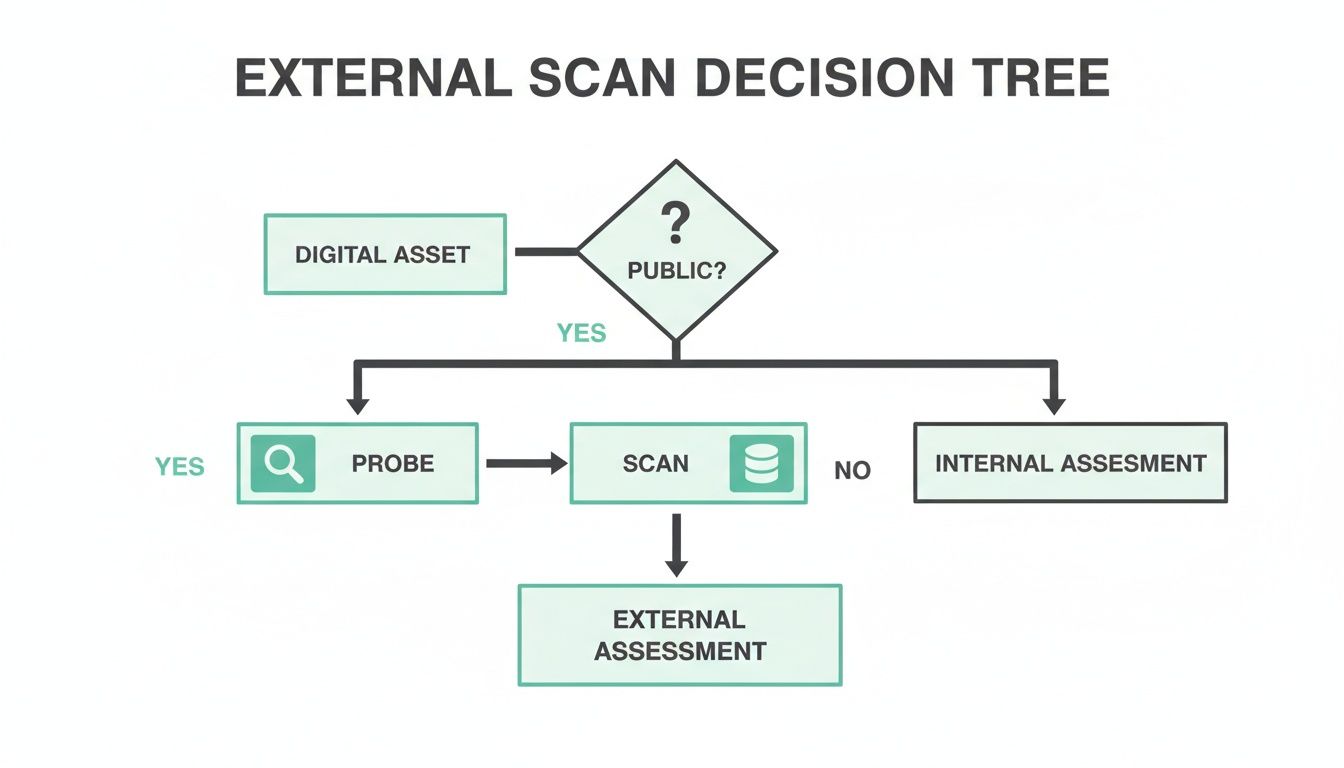
Our OSCP, CEH, and CREST certified experts perform manual pentests that are fast and affordable. We validate what’s actually a threat from scan results. This cuts out the noise that wastes your team's time.
Instead of a huge list of maybes, we give you a short report on what to fix now. You get clear results without the high price, and the full report is ready in about a week. Contact us through our form to see how our affordable pentesting can work for you.
Using External Scanning to Meet Compliance
As an IT manager or CISO, you know compliance is a must. Frameworks like SOC 2 and PCI DSS require external vulnerability scanning. Your external network is a primary target for attackers.
A stunning 30% of incidents last year came from hackers exploiting public-facing applications. This shows a direct link between what scans find and real breaches. You can dive deeper by reviewing the full threat intelligence report.
But just running a scan to check a box is not enough. Auditors want to see that you are actively managing risk, not just finding it. If you're exploring tools for frameworks like SOC 2 or ISO 27001, you might find this list of Top Vanta Alternatives for SOC 2, ISO 27001 & NIS 2 Compliance useful.
Our affordable manual pentests go beyond the checklist. We provide the detailed evidence that auditors want to see, proving you are finding and fixing real risks.
Prioritize Fixes After External Vulnerability Scanning

Getting a scan report with hundreds of "critical" findings is overwhelming. You can’t fix everything, and trying to is a waste of your team's time. We do things differently.
We don't just hand you a raw scanner report. Our manual pentest cuts through the noise. We prioritize findings based on what's truly exploitable and its business impact.
This lets your team focus on the few issues that could actually cause a breach. With over 23,000 new vulnerabilities disclosed recently, prioritization is key. You can see more in Recorded Future's vulnerability research.
A good pentest tells you what to fix now, what to watch, and what is just noise. We provide that clarity. For more on this, check out our guide on the vulnerability management process steps.
Why Our Affordable Manual Pentest Is Better
Traditional pentesting is slow and expensive. The reports are often generic lists that don't help your team. We built our service for companies that need real security validation without the high cost and long waits.
Our team of certified experts (OSCP, CEH, CREST) performs a real manual pentest. We find vulnerabilities that an attacker could actually use. We deliver clear, actionable results in about a week.
Automated scanners miss critical issues and create a lot of false alarms. We find the security gaps those tools miss and confirm what poses a real threat. This saves your engineers from chasing down hundreds of low-impact alerts.
If you need to prove your security for an audit or a client, we are the fastest and most affordable way. Contact us through our form for a simple, no-nonsense quote today.
External Vulnerability Scanning Frequently Asked Questions
How often should I run scans? We recommend running automated external scans at least weekly. This helps you catch new issues quickly. You should follow up with a manual pentest at least quarterly or annually.
Will a vulnerability scan affect my systems? No. An external vulnerability scan is non-intrusive. It’s like lightly knocking on doors to see if they're locked and won't impact your system's performance.
How is your pentest different than bug bounties? A bug bounty can be unpredictable. You might get low-quality reports or find that critical areas get no attention. Our manual pentest is a focused engagement built for your needs. We deliver a complete report in about a week, giving you the predictable, audit-ready results you need.
Ready to move beyond basic scans and get a real, human-verified pentest report in about a week? Contact Affordable Pentesting through our no-nonsense quote form.
.svg)
