A pen test tool is software an ethical hacker uses to find security holes in your company's digital assets. Think of it as a toolkit for checking the locks on your apps and networks before a real burglar tries. These tools are the workhorses behind any serious security assessment, which you’ll hear called a pentest, pen testing, or penetration test.
What Is A Penetration Test And Why Use Tools
Imagine your business is a bank. A penetration test is like hiring security experts to try and break into your vault. Instead of crowbars, they use a suite of pen test tools to simulate real-world cyberattacks. The whole point is to find vulnerabilities, like a weak digital lock or an unguarded back door, before actual criminals do.
This process is about being proactive with your security. You aren’t waiting for a breach to happen; you’re actively hunting for weaknesses to fix them first. A good penetration testing report gives you a clear, actionable plan to strengthen your defenses and avoid the nightmare of a real breach.
For many businesses, this process is also critical for compliance. Audits for frameworks like SOC 2, PCI DSS, and HIPAA almost always require regular penetration testing to prove you’re taking security seriously. Skipping it can lead to massive fines and a total loss of customer trust.
The problem is that traditional pentesting firms are known for high prices, slow timelines, and reports that are just glorified scans. They run an automated tool and call it a day, leaving you with a big bill and a false sense of security. We pair the right tools with certified professionals (OSCP, CEH, and CREST) to deliver a deep, manual pen test that finds what automated scanners miss. We deliver your report in about a week at a price that makes sense.
Exploring Different Kinds Of Pen Test Tools
Not all pen test tools are the same, just like a mechanic has different tools for different jobs. A skilled pentester uses a variety of tools during a penetration test to find specific kinds of weaknesses. One tool might map out your network, while another is built to check your website for common coding mistakes.
Understanding these categories helps you see the difference between a simple scan and a thorough, manual penetration test. A professional pentester knows how to blend these tools to get a complete picture of your security. This combination of automated tools and human expertise is why our affordable manual pentests deliver real results you can count on.
Network Scanners And Reconnaissance Tools
The first step in any pen test is gathering information. Network scanners are the main tools for this job. They map out your entire network to see what's connected, including servers, laptops, printers, and any other devices. Their goal is to find active devices, open ports, and running services.
Think of it as a security guard walking your building's perimeter and checking every door and window. This initial map gives the pentester a clear view of your company's attack surface. It highlights potential entry points for a deeper look, providing the foundation for the rest of the penetration testing.
Web Application Scanners Find Common Flaws
Websites and apps are often the most exposed parts of a business. Web application scanners are special tools designed to crawl your websites and APIs, hunting for common security flaws. They look for vulnerabilities like those in the OWASP Top 10, such as SQL injection, which can let an attacker steal data.
These tools automate checking hundreds of pages for known weaknesses, but they have limits. An automated scanner is great at finding easy targets but often misses complex business logic flaws. These are the kinds of vulnerabilities that require a human's creative thinking to find, which is why we always perform manual penetration testing. You can explore our guide on the top web application security testing tools.
Exploitation Frameworks And Manual Testing
This is where a real penetration test separates itself from a simple scan. Exploitation frameworks are advanced toolkits that let a certified pentester simulate a real attack. After a scanner flags a potential vulnerability, these frameworks are used to confirm if it can actually be exploited.
This is the "testing" part of a "pen test." Instead of just reporting a "potential" weakness, an OSCP or CREST-certified professional shows you the real-world impact. They might try to gain access to a server or pull sensitive data. This manual verification is critical, as it eliminates false alarms and shows you exactly what an attacker could do, helping you fix the most important issues first.
How To Choose The Right Pen Test Approach
Knowing about different pen test tools is one thing, but picking the right approach for your business is what matters. The decision usually comes down to three things: your compliance needs, your budget, and how fast you need a report. Whether you're an IT manager facing a SOC 2 audit or a founder needing to assure clients their data is safe, the path you choose is important.
The main options are buying your own tools, building an in-house team, or hiring an outside penetration testing provider. For most small to medium-sized businesses, the math is simple. Hiring an affordable, expert service is the fastest and most cost-effective way to get reliable results. You get certified professionals and their expensive toolkits without the massive overhead.
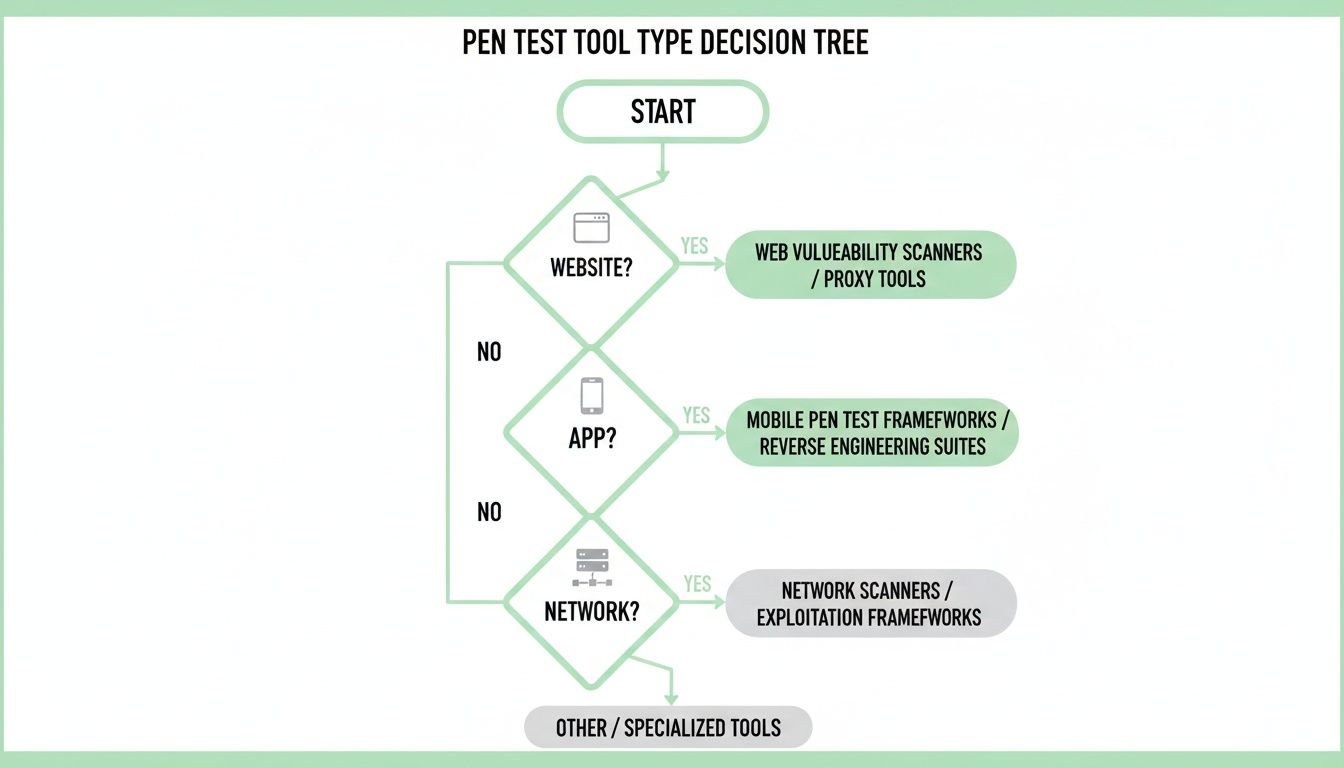
The type of asset you need to secure, like a website or network, directly influences the kind of pen test tool a professional will choose. For companies needing to comply with frameworks like ISO 27001, affordable services provide a way to simulate advanced threats without enterprise-level pricing. When designing an effective pen test, especially for larger targets, pros use techniques like proxy IP rotators) to simulate a sophisticated attacker.
Why Hiring A Pentest Service Makes Sense
Hiring a third-party provider is often the smartest choice. You get immediate access to a team of certified experts with OSCP, CEH, and CREST certifications who live and breathe security. They already have the best tools and, more importantly, the experience to find complex vulnerabilities that automated scanners always miss.
This approach is perfect for satisfying compliance requirements like SOC 2, HIPAA, or PCI DSS. Auditors want to see an independent, third-party assessment, and that’s exactly what a service provides. You get a thorough manual penetration test with a detailed report, delivered in under a week. That speed is critical when you have a tight deadline for an audit or a client request.
Integrating Pentesting Into Your Compliance Workflow
A pen test isn't just another item on your security checklist; it’s a critical piece of your entire compliance strategy. For any company needing to meet standards like SOC 2, PCI DSS, or HIPAA, a solid penetration test report is non-negotiable proof that you’re actively protecting customer data. Think of it as a mandatory inspection.
Auditors don’t just ask if you've done a penetration test, they want to see the report. They’re looking for proof of both automated scanning and, more importantly, in-depth manual testing. A simple scan report just won’t cut it. They need to see that a certified human expert tried to break in, because that’s exactly what a real attacker would do.
Failing to provide a proper pen test report can block deals, cause you to fail an audit, and lead to heavy fines. That’s why a thorough penetration test is a business enabler, not just a security expense. For a deeper dive, check out our guide on how penetration testing fits into SOC 2 compliance. The overall pentest market is projected to grow from USD 2.0 billion to USD 8.7 billion by 2034, driven almost entirely by this need for compliance. You can learn more about these market trends and insights at dimensionmarketresearch.com.
Meeting Audit Deadlines Without The Stress
We know audit timelines can be brutal. You often need a comprehensive penetration test completed with a full report in hand before a deadline that’s just weeks away. Traditional pentesting firms can take months to schedule a test and deliver a report, creating a massive bottleneck for your compliance team.
This is where speed and affordability make all the difference. Our process is built to eliminate that stress by delivering a complete, audit-ready manual penetration test report in under a week. This lets you get the evidence you need for your auditors without derailing your entire schedule. You get a clear, actionable report from OSCP and CREST-certified professionals who know exactly what auditors are looking for.
Why Manual Pentesting Finds What Tools Miss

Automated pen test tools are fantastic for catching the usual suspects. They’re fast and great at spotting common vulnerabilities, but they have a critical blind spot: they can't think. An automated scanner is like a security guard who only checks a predefined list of unlocked doors. This is where a manual penetration test changes the game completely.
A manual pentest injects human intelligence and creativity into the security assessment. Our certified pentesters act like master locksmiths; they don’t just check the doors, they jiggle the handles and look for clever ways to bypass the alarm system. This hands-on approach is the only way to find complex vulnerabilities that automated scanners are programmed to ignore, such as business logic flaws.
These are vulnerabilities that exist within the intended workflow of an application. An automated tool can’t spot them because, technically, the application is working as designed, just not securely. For example, a tester might find they can change an item's price in their shopping cart by manipulating the data sent to the server. These are the kinds of critical findings that lead to major financial or data loss, and they require a human to discover them. If you want to dig deeper into the limitations of automation, you can learn more about how it compares to a manual approach in our guide to automated pen testing.
Get Your Fast And Affordable Pen Test Report
Ready to secure your business and hit your compliance goals without the frustration? The old pentesting model is broken. It’s slow, expensive, and leaves you with reports that are nearly impossible to understand. We do things differently by focusing on affordable manual pentests with a lightning-fast turnaround.
You get a comprehensive report from certified professionals in a week, not months. The report gives you clear, actionable steps to fix every vulnerability we find, so your team knows exactly what to do next. If you need a reliable pen test without the enterprise price tag, it's time to get started.
Our approach is built for speed and clarity. We pair the best pen test tools with the expertise of our certified ethical hackers. Every engagement is a manual penetration test, not just an automated scan. This human-led process ensures we uncover the critical issues that scanners always miss, giving you a true picture of your security posture. You tell us what you need tested, we give you a clear quote, and our OSCP, CEH, and CREST certified team gets to work.
Your Actionable Report In Under A Week
The most important part of any pentest is the final report. This is what you'll use to strengthen your defenses and prove compliance for frameworks like SOC 2 or PCI DSS. We deliver a high-quality, easy-to-understand report in about a week. It’s written for humans, with a sharp executive summary for leadership and detailed technical findings for your developers.
Each vulnerability is explained, ranked by risk, and comes with step-by-step guidance on how to fix it. There’s no fluff and no jargon, just a clear roadmap to better security. Reach out through our contact form to get a quote and see how simple this process can be.
Your Top Penetration Testing Questions
Got questions about pen testing? Here are straight answers to the questions we hear most often.
A vulnerability scan is an automated checklist that quickly looks for known security flaws. It's a useful first step but generates a lot of false alarms. A penetration test is a deep dive by a human expert. A scan tells you a door might be unlocked; a pen test confirms someone got in and read your sensitive files, which is why auditors for SOC 2 or PCI DSS demand a full penetration test.
You should get a full penetration test at least once a year. That’s the industry standard and what most compliance frameworks require. You should also get one after any major change to your applications or network, like a new product launch or a big code overhaul. Regular testing is a critical part of keeping your defenses strong as your business grows.
A good penetration test report is clear, concise, and actionable. It will list every vulnerability we found, rank each one by severity, and provide clear, step-by-step instructions on how to fix everything. Our reports are delivered by OSCP, CEH, and CREST certified experts and are designed to be understood. We get them to you in under a week so your team can start plugging holes immediately.
Ready for a pen test that’s fast, affordable, and delivers a report you can actually use? At Affordable Pentesting, we provide high-quality manual penetration tests with reports in about a week. Get the security validation you need without the high costs and long waits. Get your quote today!
.svg)
