Confused about penetration tests versus vulnerability assessments? A vulnerability assessment is an automated scan that finds potential problems, like an open window. A penetration test is a real person trying to climb through that window to see what they can steal.
Tired of slow, expensive security firms that deliver confusing reports? We provide affordable manual pentests with clear, actionable results in under a week, so you can meet compliance and actually secure your business.
Stop Guessing About Your Security Risks
You need to know if you have real security holes, not just a long list of maybes. Especially when you're facing a SOC 2 audit or another compliance deadline. You don't have time for confusing reports that cost a fortune and take weeks to arrive.
This guide skips the technical jargon. We'll show you the difference between a scan and a real pentest so you can choose the right one for your business. You'll get the security you need without the high price or long wait.

While testing your network is key, remember that security also applies to old equipment. Using secure data destruction practices to prevent data breaches is just as important for protecting your company's information.
What is an Automated Vulnerability Assessment?

Think of a vulnerability assessment as an automated security checkup. A scanner quickly looks over your systems for thousands of known weaknesses, like missing software updates or bad server settings. It’s like a spell-checker for your security.
The final report is a list of potential issues ranked by how serious they might be. It’s a good first step to see where you might be weak. These scans are fast, affordable, and great for regular check-ins to catch easy-to-fix problems.
But because it's automated, the scanner can't prove a vulnerability is actually a real threat. You might get false positives, which are flagged risks that a real hacker can't use. You can read more about this in our guide on what is a vulnerability assessment.
A vulnerability assessment is a great starting point, but it doesn't try to actually break in. It just gives you a list of possibilities. That's where a real pentest comes in.
What is a Real-World Penetration Test?

A penetration test, or pentest, is a simulated cyberattack on your business. Instead of just a list of potential problems, one of our certified ethical hackers acts like a real attacker. They actively try to exploit weaknesses to see how far they can get into your systems.
This manual, human-led approach finds complex security issues that automated scanners always miss. The goal isn't just to find one bug, but to show the real business damage a breach could cause, like stealing customer data. Learn more in our guide on what is penetration testing.
Think of it as the ultimate stress test for your security defenses. It's also a must-have for compliance standards like SOC 2 and PCI DSS. Things like knowing how to prevent Man-in-the-Middle attacks show why this hands-on testing is so important.
A skilled pentester thinks like an attacker, combining small issues to create a major security hole. That’s something a scanner can't do. Our pentesters are certified professionals with OSCP, CEH, and CREST certifications, so you know you're getting a true expert.
What is the Real Difference Between Scans vs Tests?
The difference is simple. A vulnerability assessment gives you a long list of potential security problems. A penetration test confirms which of those problems can actually be used by a real attacker to break in.
A vulnerability scan is an automated checklist that gives you a quick overview. It's a good starting point. A pentest is a simulated mission where a certified expert thinks like a hacker to find out what damage they could really do.
Let’s break down the key differences so you can decide which one your business needs right now.
Comparing Vulnerability Assessments to Penetration Tests
This table shows the core differences between a vulnerability assessment and a penetration test. It will help you quickly see which one fits your needs.
So, a vulnerability scan answers, "What known weaknesses might I have?" It’s fast and affordable, giving you a baseline for your security.
A penetration test answers the real question: "How would a real attacker get in, and what could they steal?" Our experts don't just find one issue; they show you the true business risk. This is exactly what auditors for SOC 2 and other frameworks require.
How To Choose The Right Test For Your Business
So, which one do you need? It all comes down to your goals, budget, and compliance needs. One isn't better than the other; they just solve different problems.
If you're a startup just starting your security program, regular vulnerability scans are a smart, affordable first step. They give you a quick and cheap way to manage risk. Learn more about how they work in our post on external vulnerability scanning.
But if you need to pass a SOC 2 or PCI DSS audit, a manual penetration test is required. Auditors demand proof of a real-world attack simulation by a human expert. An automated scan just won't cut it.
This decision tree can help you see which path makes sense for you.
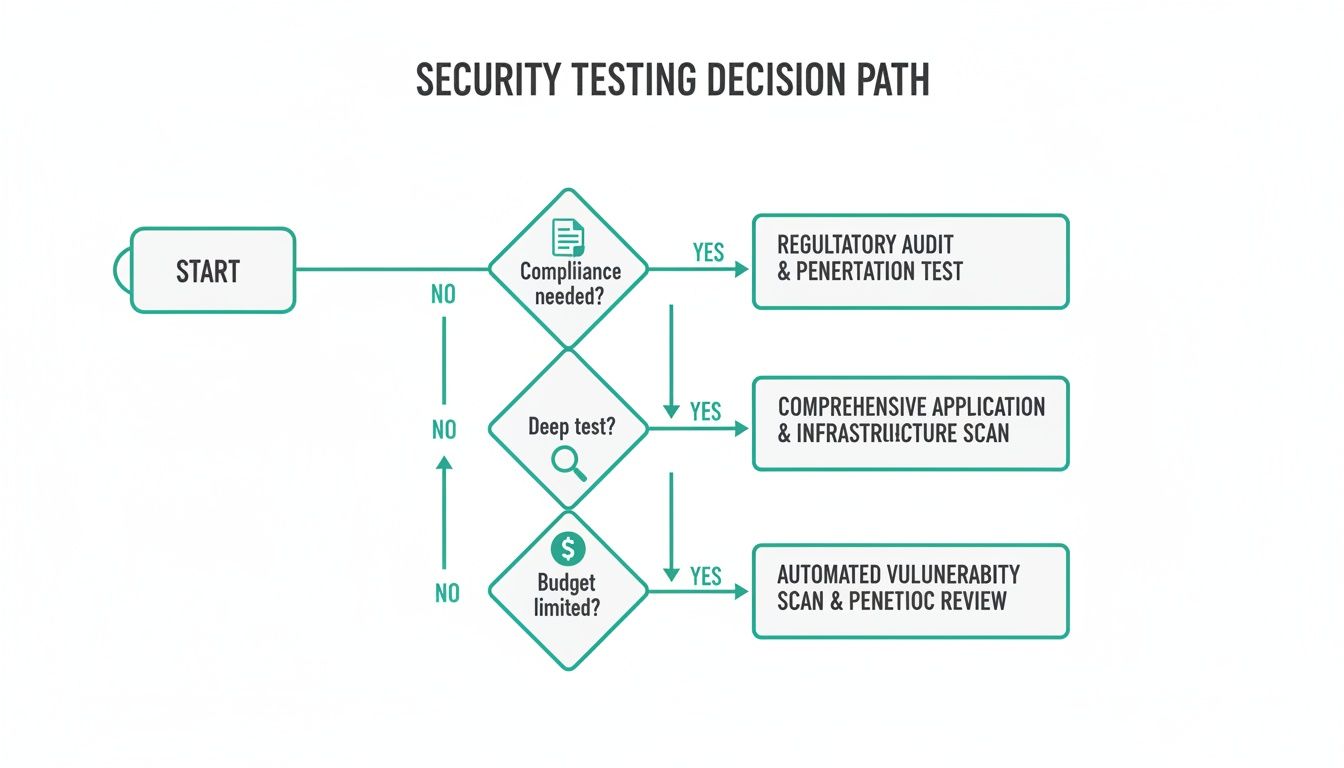
As you can see, if compliance is your goal, you need a pentest. If you just need continuous monitoring on a tight budget, vulnerability scanning is a good place to start. The best security programs use both.
Why Our Affordable Pentests Make Sense
Let's be direct. Traditional pentesting is slow, expensive, and often gives you a confusing report your team can't use. We fixed this broken model. We are the affordable alternative for startups and small businesses.
You get a real security assessment from certified professionals. Our team holds top certifications like OSCP, CEH, and CREST. They focus on manual, human-driven testing that finds the critical flaws automated scanners always miss.
We deliver a clear, actionable report in under a week. This means your team can start fixing real problems right away instead of waiting months.
Best of all, our affordable price includes a free retest. After your team patches the issues, we go back in to confirm the fixes work. This gives you the proof you need for auditors and compliance, all at a price that makes sense.
Ready to see how a pentest should work? Get in touch through our contact form and we'll show you.
Your Pentest vs Vulnerability Scan Questions Answered
We get these questions all the time. Here are the simple, no-nonsense answers to help you decide what’s right for your company.
How Much Does a Penetration Test Cost?
A vulnerability scan is always cheaper upfront because it's automated. But a manual penetration test provides much more value by confirming which vulnerabilities are real threats. This saves your team from wasting time on false alarms.
Our pentests are priced for startups and small businesses. You get real, actionable findings without the huge enterprise price tag. We are the affordable pentesting solution.
How Often Should We Run These Tests?
Think of vulnerability scans as an ongoing health check. Running them monthly is a good way to catch new issues.
A full manual penetration test is like an annual physical. It's the deep-dive required once a year for compliance like SOC 2 or PCI DSS. Many clients also get one after a major software update to make sure no new security holes were created.
What Should I Expect From the Report?
A vulnerability scan report is a long, automated list of potential problems. It's often full of noise and things that aren't real risks.
Our penetration test report is different. You get a clear, human-written summary of confirmed security holes. We deliver it in under a week with simple steps to fix what actually matters, so your team can get to work immediately.
Ready to stop guessing and get real answers about your security? Affordable Pentesting delivers fast, expert-led manual pentests that satisfy auditors and fit your budget. Get in touch through our contact form to see how simple and affordable real security can be.
.svg)
