Penetration testing is no longer a luxury for your clients. Auditors and cyber insurance carriers now require it, and if you can't provide fast, affordable reports, you risk losing accounts to competitors who can.
Your Clients Need Pentests for Compliance
The penetration testing market has shifted a lot in recent years. What was once something only large enterprises invested in is now a basic requirement for small and mid-sized businesses as well. This has become the standard way companies prove they are operating securely.
Clients in industries like finance, healthcare, and SaaS are feeling this pressure the most. Auditors and cyber insurance providers increasingly require an up-to-date penetration test before approving coverage or allowing new contracts to move forward. When these companies reach that point, they will need a trusted provider quickly. That provider should be you.
Offering Pentesting Services Protects Your Business
Adding pentesting is a smart move to keep and grow your client base. It changes your role from just "the IT guys" to an important security partner who helps their business succeed. You solve a critical problem for them right when they need it most.
Instead of your client searching for an unknown, expensive security firm, you become their trusted solution. This makes your MSP's services incredibly sticky and hard to replace. It's about client retention, not just another revenue stream.
Why MSPs Should Offer Pentesting Services
Offering pentesting changes the conversation completely. You are now helping your clients pass audits, get funding, and land bigger customers. Your work directly impacts their bottom line and business growth.
This lets you have better conversations with your clients. You can help them get SOC 2 certified or unblock their cyber insurance renewal with an affordable pentest. This makes you a strategic advisor, not just a tech. For more details, see our guide on the role of pentesting in SOC 2 compliance.
Pentesting Focus for Different Compliance Frameworks
Different compliance rules need different kinds of pentests. You don't need to be a hacking expert, but knowing the basics helps you guide clients. A client needing a SOC 2 audit has different needs than one focused on HIPAA.
Here is a simple table showing which pentests are usually needed for common compliance standards your clients face. Partnering with a specialized firm lets you bring in certified OSCP, CEH, and CREST pros when you need them.
Compliance FrameworkPrimary Pentest FocusCommon Client IndustrySOC 2Web Application, External Network, Cloud Config ReviewSaaS, Technology, B2BPCI DSSExternal & Internal Network, Web ApplicationE-commerce, RetailHIPAAExternal Network, Web Application, Internal NetworkHealthcare, Health Tech
Structuring Your MSP Pentesting Business Model

To make pentesting profitable, you need a smart and scalable business model. You have two main options. You can build an in-house team from the ground up, or you can partner with a firm that already has the experts.
Let's be direct. Building your own pentesting team is a huge task. It's slow, expensive, and often distracts from your main MSP business. You need a team of certified professionals, not just one person.
Choose a Smart Pentesting Delivery Model
For most MSPs, partnering is the faster and more practical choice. A white-label or referral partnership lets you offer high-quality pentesting services right away. You avoid the huge salaries and training costs.
You can rely on a partner’s certified experts, proven tools, and established reporting. This means you can start selling and delivering audit-ready reports to your clients within a week. You get all the credit without the operational headaches.
Partnering vs Building an In-House Team
When you compare the real costs and benefits, the choice is clear. An in-house team is a major expense with ongoing costs. A partnership is built on scalable, on-demand costs that match your sales.
Here is a simple side-by-side comparison to make it easy. The partnership model is the most logical path for any MSP focused on profit and client happiness. It removes the risk and lets you deliver value much faster.
FeatureIn-House TeamPartnership ModelInitial CostHigh (recruiting, salaries, tool licenses)Low to none (no hiring or software costs)Time to Market6-12 months (hiring, training, process building)Immediate (you can start selling this week)Required ExpertiseYou must hire and retain OSCP, CEH, CREST expertsProvided by the partner on demandScalabilityDifficult (hiring is slow and competitive)Easy (scale up or down with client demand)Operational OverheadHigh (managing staff, training, tools, reporting)Minimal (partner manages the entire pentesting workflow)
Create Simple and Smart Pricing Strategies
Your pricing needs to be simple and built around solving your clients' problems. Offer straightforward packages that address specific needs, like passing a SOC 2 audit or renewing cyber insurance. This makes buying from you an easy decision.
Consider offering a couple of core pricing models. A one-off pentest is a flat-fee service for clients who need a single test. An annual recurring package is great for clients with ongoing compliance needs and builds predictable revenue for you. Your goal is to make pentesting an easy "yes." To learn more about pricing factors, see our guide on how much penetration testing costs.
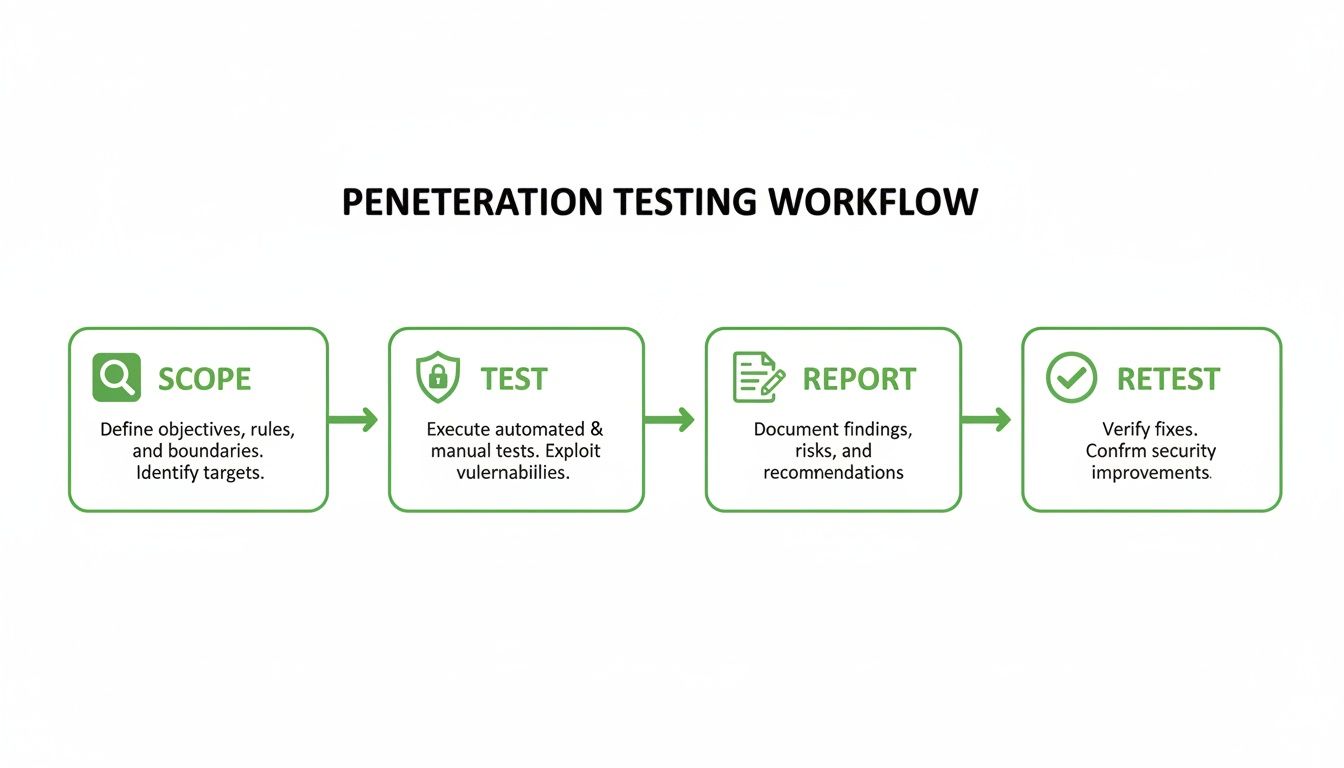
A Pentesting Workflow That Actually Works
Forget the long, complicated pentesting processes from big security firms. For MSPs and your clients, the process needs to be lean, fast, and repeatable. A great pentesting for MSPs service follows a simple four-step process.
This process strips away the fluff and delivers exactly what your clients need. They get a credible report, fast. It's about efficiency and getting the job done right so they can meet their deadlines.
Phase 1 Nailing Down The Project Scope
Scoping should be a quick and efficient call with your client. The goal is simple. Figure out exactly what needs to be tested to satisfy their auditor, client, or insurance provider.
You are just answering three basic questions. What are we testing? What is the goal? What is the deadline? Keeping the scope tight lets you lock in a fixed price and a clear delivery date right away.
Phase 2 The Manual Pentest Itself
Once the scope is approved, the real work begins immediately. This is where partnering with a team of certified pros is a huge advantage. A team of OSCP, CEH, and CREST certified pentesters simulates a real-world attack.
This is not just an automated scan. It's a hands-on, manual process where experts find complex flaws that automated tools miss. This is what gives the final report credibility with auditors and stakeholders.
Phase 3 Fast And Actionable Reporting
The report is the most important part of the service. Your edge is delivering a clean, actionable report within a week of the test finishing. A great report has two parts.
First is a high-level executive summary in plain English that explains the business risk. Second are the technical details the dev team needs to fix the problems. This document is the proof they need to pass their audit.
Phase 4 Free Remediation Re-Testing
Delivering the report is not the final step. You have to prove the vulnerabilities were fixed to close the loop for compliance. Offering a free remediation re-test is a huge value-add and a powerful selling point.
After the client's team fixes the issues, the pentesters check again to verify the fixes. This gives the auditor the final proof they need. Using a workflow documentation template can help keep this process smooth every time.
Why Certified Experts Beat Automated Tools
Your clients need a pentest they can trust. A cheap report from an automated scanner often isn't enough for an auditor. You can show real value by explaining the difference between a real manual pentest and a simple automated tool.
Automated scanners are fast but have a huge blind spot. They are bad at finding business logic flaws or anything that requires human creativity. Think of it like this, an automated tool checks if a door is unlocked, but it can't convince someone to open it.
The Power of a Human Hacker
A certified penetration tester thinks like a real attacker. They don't just follow a checklist. They adapt and connect small issues to find major security breaches. Software simply cannot do this.
This is critical for your clients because auditors and compliance frameworks like SOC 2 know the limits of automated tools. They want to see proof that a human expert has rigorously tested the system. An automated scan finds known problems, but a manual pentest discovers unknown risks.
Manual Pentesting Versus Automated Scanning
It is important to understand the value each approach offers, especially for compliance. Automated scans have a place, but they are no substitute for the deep analysis of a manual test. For any client facing an audit, a manual pentest is a requirement.
FeatureManual PentestingAutomated ScanningFindingsDiscovers complex, business-logic, and chained vulnerabilities. Zero false positives.Finds known, common vulnerabilities (low-hanging fruit). Often has high false positive rates.CostHigher initial cost due to expert time and effort.Lower cost, often subscription-based.Compliance ValueThe "gold standard" required for SOC 2, PCI DSS, and HIPAA. Satisfies auditors.Generally insufficient for most compliance audits. Seen as a baseline check, not a true test.MethodologyCreative, adaptive, and mimics real-world attackers.Follows a predefined, rigid set of rules and signatures.ReportingDetailed, contextual, with actionable remediation guidance.Generic, often overwhelming lists of potential findings without context.
Why Certifications Like OSCP And CEH Matter
What do acronyms like OSCP, CEH, and CREST really mean? Think of them as a pilot's license for ethical hacking. These are hands-on tests that prove a pentester has the skills to simulate a real cyberattack.
When you partner with a provider whose team holds these certifications, you are bringing in proven experts. You can confidently tell your clients their systems are being tested by professionals. Learn more about the differences in our article on security testing automation tools or see how some tools like automated website testing tools can help.
How to Sell Pentesting to Clients
Selling pentesting doesn't have to be hard. Your clients are buying solutions to business problems, not technical jargon. Your sales plan should be built around solving those problems with simple language.
Stop talking about "SQL injection" and start talking about "getting you ready for your SOC 2 audit." This changes the conversation from a technical one to a clear business solution. Your job is to make it simple for them to buy from you.
Frame The Conversation Around Business Outcomes
Your clients need a pentest for a reason. It could be to renew their insurance, pass a SOC 2 or HIPAA audit, or land a new customer. Your sales pitch must start there.
Lead with the outcome they want, not the technical details. This shows you understand their world and makes your service the immediate fix for their problem. Nobody buys a pentest, they buy a passed audit, a renewed policy, or a closed deal.
Create Simple Easy-to-Sell Service Packages
Forget about complex custom quotes that take weeks. Your clients need clear, predictable pricing. Creating straightforward service packages is the fastest way to make your offering a no-brainer.
Think about offering flat-fee packages like a "Compliance-Ready Pentest" or a "Cyber Insurance Pentest." These packages make the buying decision incredibly easy. You present a clear solution to a clear problem for a fixed cost.
Communicate Value and Your Key Differentiators
Your advantage is that you offer pentesting without the problems of old, slow, and expensive firms. Your messaging should focus on three key points: affordability, speed, and expertise.
Explain that you deliver what they need without the enterprise-level price tag or the month-long wait. This is a huge win for startups and SMBs with tight budgets and deadlines.
Leverage Reports As Powerful Case Studies
Every successful pentest is a potential marketing tool. A clean report is powerful proof of your client's strong security. You can ask for permission to create an anonymous case study to show new prospects.
Real-world examples are more persuasive than any sales pitch. They provide social proof and show you can deliver on your promises. To start building these wins, contact us through our form to see how a partnership works.
Or Work with MSP Pentesting
If you need an MSP/channel only partner our sister company MSP Pentesting may be a better fit for your business.
How Much Should We Charge Clients?
This depends on the scope, but your goal is to be affordable for SMB clients. Forget the $15,000+ quotes from traditional firms. You can offer a price that solves their problem without breaking their budget.
A great strategy is to create fixed-price packages for common needs like SOC 2. This transparency builds trust and makes selling easier. By working with an affordable partner, you can add a healthy margin while delivering great value.
What if a Pentest Finds Nothing?
This is a common worry but rarely happens with a thorough manual pentest. If it does, that's great news. A clean report from ethical hackers is powerful proof that their security is solid.
You can frame this as a validation of their security investments and your work as their MSP. It becomes a valuable document for auditors, customers, and insurance carriers. A quality partner provides a detailed report outlining the methodology, so the client gets proof of the work.
How Do We Explain Technical Findings?
A good pentesting partner does this for you. Their report should always include a high-level executive summary in plain English. This summary focuses on business risk, not technical jargon.
For example, instead of "cross-site scripting," the summary might say, "We found a flaw that could let an attacker steal login details." You can walk your client through this summary and hand the technical details to their developers. It’s that simple.
How Long Does a Pentest Take?
Speed is your secret weapon in the pentesting for MSPs market. While traditional firms can take a month or more, you should aim for a one to two-week turnaround from kickoff to final report.
This fast timeline is a huge selling point for clients with tight deadlines. It shows you respect their time and can solve problems quickly. This sets you apart from slower, more bureaucratic competitors.
Ready to add fast, affordable, and expert-driven pentesting to your MSP’s offerings? Affordable Pentesting makes it simple to provide the audit-ready reports your clients need without the high costs or long waits.
Contact us through our form to see how a partnership can work for you.
.svg)
