A vendor risk rating is a security report card for your partners. It quickly shows you which vendors are safe and which ones might be leaving your digital doors unlocked, helping you avoid costly breaches caused by insecure third-party tools.
What Is a Vendor Risk Rating?
Think of your company as a locked house. You have strong doors and windows, but you give a key to a cleaning service. If that service is careless and leaves the back door open, your house is no longer secure. A vendor risk rating tells you how trustworthy that cleaning service is before you hand over the key.
This rating is a simple score that measures the security risk each vendor brings to your business. It's not just paperwork. It's a crucial tool for protecting your company and meeting compliance standards like SOC 2, HIPAA, or PCI DSS.
A single insecure vendor can become your biggest problem. Data shows that breaches caused by third parties are incredibly common and expensive. A good vendor risk rating system helps you spot these issues before they turn into disasters.
To get a handle on risk ratings, start by understanding vendor due diligence. A rating is the final score from that process, turning complex data into a clear action plan. Our guide on third-party risk assessment explores this in more detail.
How to Determine a Vendor's Risk
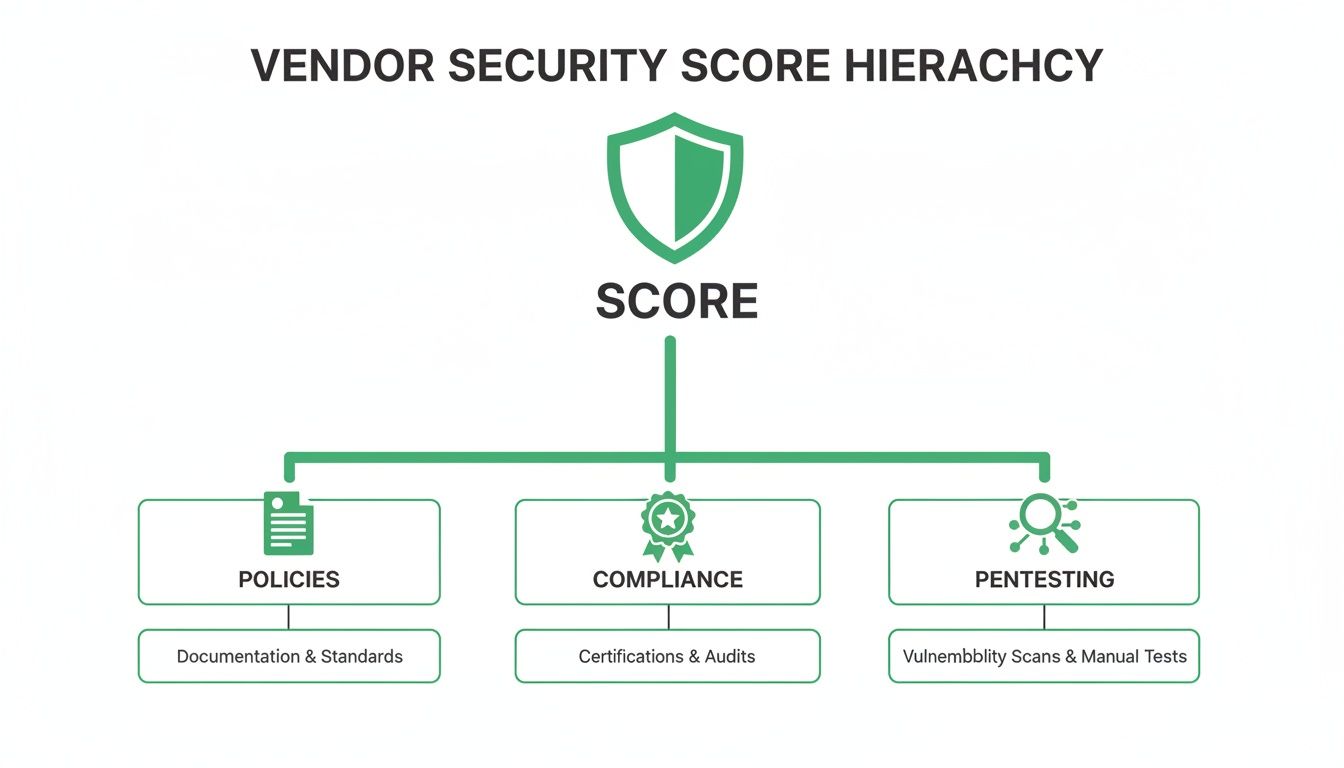
Figuring out a vendor's risk is like checking a student's report card. You look at a few key subjects to get the full picture of their security health. Some information comes from their policies, while other proof comes from certifications or a real-world security test.
First, look at their security rulebook. A vendor who can't show you written security policies is a huge red flag. Ask to see their data protection rules, incident response plan, and employee training documents. This is the absolute baseline for any assessment.
Certifications like SOC 2 or ISO 27001 are also important. They prove an independent auditor has checked their security and confirmed it meets industry standards. It's a strong sign they take security seriously.
Also, check their history. Have they had a data breach before? A vendor's past can tell you a lot about their future performance. The global vendor risk management market research shows how critical this has become for businesses everywhere.
Why Pentesting Is a Critical Step

A vendor can have great policies and certifications, but what if their app is full of holes? The only way to know for sure is to test it. This is where penetration testing comes in. It’s like hiring a professional to check the locks on that vendor’s doors.
A penetration test gives you an unbiased, real-world look at a vendor's defenses. Our certified ethical hackers (OSCP, CEH, CREST) find the real weaknesses that questionnaires and automated scans almost always miss. You get a detailed report in a week, not months.
A pentest report with zero critical findings is the strongest proof you can get of a mature security program. It turns your vendor risk rating from a guess into a fact. If you need this kind of proof for your vendors, fill out our contact form to learn more.
How to Build a Simple Rating Matrix
Creating a system to score vendors doesn't have to be complicated. You can build a simple vendor risk rating matrix that turns security information into a clear score. It helps you see at a glance who your riskiest partners are.
Start by defining your risk categories. Think of it like a stoplight: red for high risk, yellow for medium, and green for low. Make your definitions clear so anyone in your company can understand them.
High-risk vendors have access to your most sensitive data, like customer PII or financial records. Low-risk partners have limited access to non-sensitive information and can prove their security with clean audit reports or recent pentest results.
Next, turn those categories into numbers. Assign points to different risk factors, where more points equal more risk. For example, does the vendor have a SOC 2 report? A "yes" could be 1 point, while a "no" is 3 points. Add up the points to get a final score. For more ideas, check out our cybersecurity risk assessment template.
A Plan for Managing High-Risk Vendors
If your rating matrix flags a vendor as high-risk, don't panic. This isn't an automatic goodbye. It's the start of an important conversation about security. The goal is to work with your vendor to fix their defenses and make your partnership stronger.
Start by sharing the specific findings from a penetration test report. A professional report from one of our OSCP or CEH certified testers gives you objective, factual evidence. It shifts the discussion from a complaint to a list of concrete issues to solve.
Next, agree on a realistic timeline for fixes. Critical flaws need to be handled immediately, while lower-risk items can be addressed over a few weeks. A remediation plan without a deadline is just a suggestion. Firm but fair timelines create accountability.
Finally, you must verify the fixes. When a vendor says an issue is resolved, you can't just take their word for it. A fast, affordable re-test from us confirms the security gap is truly closed. This is the most critical part of the process. If you need to verify a vendor's fixes, reach out through our contact form.
How to Scale Your Vendor Risk Program
As your business grows, so does your list of vendors. The simple checklists you used before can quickly become overwhelming. The key is to build a simple, repeatable system that grows with you without needing a huge budget or a dedicated team.
A well-organized spreadsheet can be the command center for your entire vendor risk program. Create a simple tracker with columns for each vendor's name, risk rating, and the date of their last security review. Use formatting to highlight vendors that need your attention.
The heart of any scalable program is consistency. Every new vendor must go through the same evaluation process. This ensures you never miss a critical security check and all your ratings are fair. It's also worth understanding the bigger picture of vendor management best practices to refine your process.
With trends in vendor risk management market analyses showing increased focus on supply-chain security, having a scalable process is key. Our affordable penetration testing services can easily integrate into your workflow.
Your Vendor Risk Rating Questions Answered
Getting a vendor risk rating system started can feel like a huge project, but it’s more straightforward than you think. Here are direct answers to common questions from IT managers, CISOs, and founders.
How often should we update ratings? For high-risk vendors, check them at least once a year. For medium and low-risk vendors, every 18 to 24 months is usually fine. If a vendor has a security breach, you must reassess their risk immediately.
What is the difference between an assessment and a rating? The risk assessment is the detective work where you gather all the evidence. The vendor risk rating is the final, simple score like "High" or "Low" that comes from all that work.
Can we work with a high-risk vendor? Yes, but you need to be careful. A high-risk rating is a signal to put extra security measures in place. If the vendor is willing to work with you to fix the issues, the relationship can work. If not, it's time to find a more secure alternative.
At Affordable Pentesting, we turn vendor security from a guess into a fact. Our fast, affordable penetration testing services give you the objective proof you need to build a vendor risk rating system you can trust. Get your report in a week, not months. Secure your supply chain by visiting us at https://www.affordablepentesting.com.
.svg)
