Handling credit card payments means you must follow PCI DSS compliance rules to protect customer data. For many businesses, proving compliance with penetration testing is slow and expensive, but ignoring it isn't an option. We provide fast, affordable manual pentests from certified experts, with reports delivered in a week so you can secure your systems and get back to business.
Your No-Nonsense Guide To PCI DSS Compliance

Think of PCI DSS as the security rulebook for handling payment card data. It was created by Visa, Mastercard, and other major card brands to protect customer information from theft. If you accept, process, or store credit card data, these rules are mandatory.
The official name is the Payment Card Industry Data Security Standard. It applies to organizations worldwide, no matter the size. If your business touches customer card data in any way, you are responsible for keeping it secure.
These rules evolve to keep up with new threats. The latest version, PCI DSS 4.0, introduced 64 new requirements to address modern attack methods. These updates become mandatory by March 31, 2025, which means businesses need a clear plan to meet them.
Ignoring PCI compliance is expensive. Fines can start at $5,000 per month and increase quickly. We make compliance easier with fast and affordable penetration testing from certified experts with OSCP, CEH, and CREST credentials, delivering a clear report in about a week.
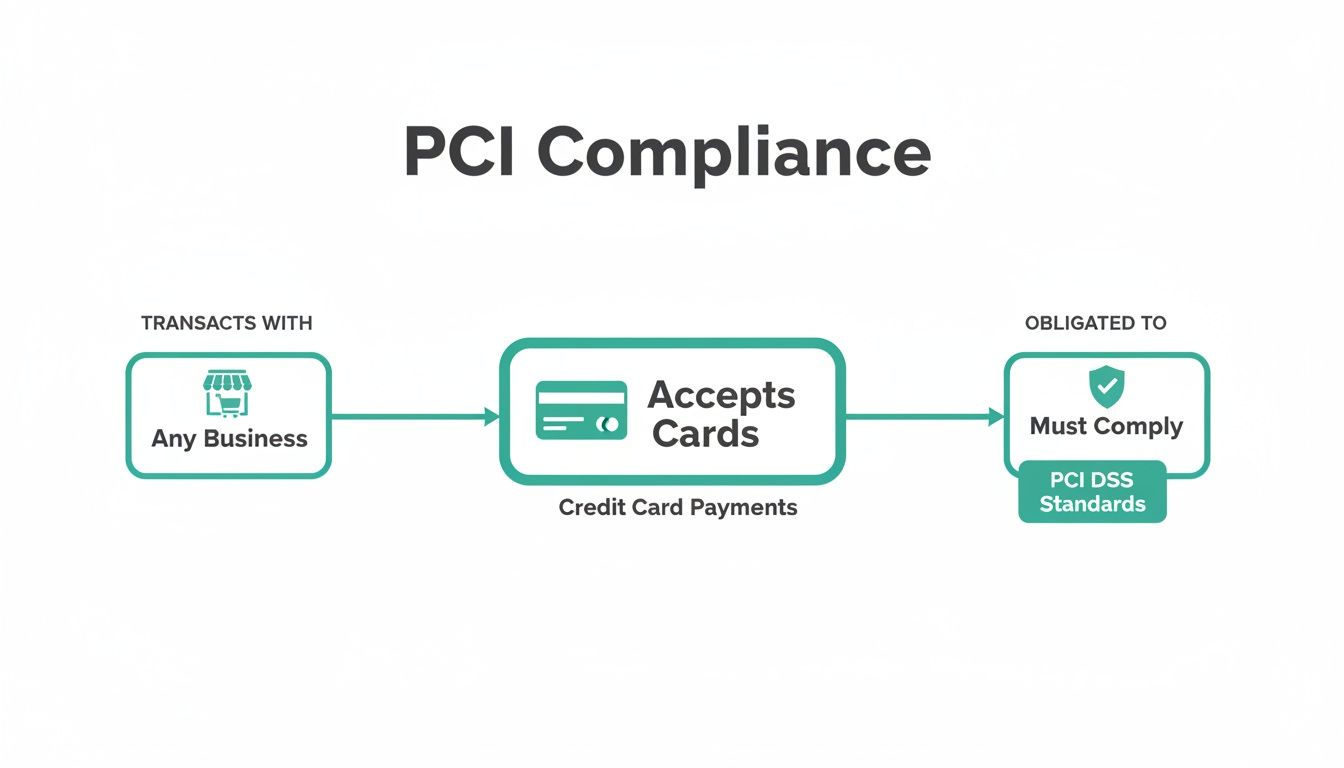
Who Needs To Be PCI DSS Compliant
Who Needs to Be PCI DSS Compliant
The answer is straightforward. If your business accepts, processes, stores, or transmits credit card data in any form, PCI compliance applies to you. Company size or revenue does not matter.
Everyone from large e commerce platforms to small local shops must follow these standards. The PCI Council groups merchants into four levels based on annual transaction volume. Higher volume merchants face more validation requirements.
Level 1 merchants process over 6 million card transactions per year.
Level 2 merchants process between 1 and 6 million transactions annually.
Level 3 merchants handle 20,000 to 1 million e commerce transactions.
Level 4 merchants process fewer than 20,000 e commerce transactions per year.
Even Level 4 merchants are required to comply. While validation steps may be simpler, the core security requirements remain the same. Small businesses often underestimate this. Our detailed guide on PCI compliance for small businesses breaks this down further.
Learn more here: PCI compliance for small businesses in our detailed guide.
The 12 PCI DSS Security Requirements
The 12 PCI DSS requirements are the foundation for securing customer data. They are grouped into six main goals that cover everything from network security to security policies. Let's break them down into simple terms.
1. Install and Maintain Firewalls: Your firewall is the security guard for your network. It blocks unauthorized traffic from getting in or out.
2. Use Secure System Configurations: You must change all default passwords like "admin" on your routers, servers, and software. Hackers love finding these easy ways in.
3. Protect Stored Customer Data: If you store card data, you must make it unreadable using tools like encryption. If a hacker steals it, they only get useless code.
4. Encrypt Data During Transmission: When you send card data over the internet, it must be encrypted. This is what SSL/TLS certificates do for your website.
5. Protect Systems from Malware: You must install and regularly update anti-virus and anti-malware software on all your systems to block known threats.
6. Develop Secure Systems and Software: Keep all your software and operating systems updated with the latest security patches to close known security holes.
7. Restrict Access to Cardholder Data: Only employees who absolutely need cardholder data to do their jobs should have access to it. This limits your risk.
8. Identify Users and Authenticate Access: Every person who can access your systems needs a unique user ID and a strong password. This creates an audit trail.
9. Restrict Physical Access to Data: You must physically secure computers, servers, and even paper documents that contain sensitive data behind locked doors.
10. Log and Monitor All System Access: Keep detailed logs of who accesses what and when. Reviewing these logs helps you spot suspicious activity early.
11. Test Security of Systems Regularly: This requires regular vulnerability scans and penetration tests to find and fix security weaknesses before attackers do.
12. Maintain an Information Security Policy: You need a formal security policy that outlines the rules for all employees and contractors, so everyone knows their role in protecting data.
For a deeper look, check out our PCI DSS compliance checklist that covers these requirements.
How To Easily Prove Your PCI Compliance
Securing your systems is only the first step. The next is proving compliance to banks and card brands. This process is called validation, and it depends on your merchant level.
Most small and mid sized businesses complete a Self Assessment Questionnaire, or SAQ. This is a structured checklist confirming you meet PCI requirements.
Level 1 merchants must undergo a much more detailed on site audit performed by a Qualified Security Assessor. This results in a formal Report on Compliance.
In addition to annual validation, most merchants must complete quarterly network vulnerability scans conducted by an Approved Scanning Vendor. These scans look for known weaknesses on internet facing systems.
A penetration test is also required. A pentest simulates a real attack by a certified ethical hacker. Our OSCP, CEH, and CREST certified testers find the complex vulnerabilities automated scans miss. Our guide to PCI DSS penetration testing explains this process in more detail. PCI DSS penetration testing in our guide.
Your Step-By-Step Path To Compliance

Getting PCI DSS compliant follows a clear four step cycle. It is an ongoing process, not a one time task.
- Define Your Scope
Identify every system that handles card data. This is your Cardholder Data Environment. Reducing this scope lowers cost and risk. - Conduct a Gap Analysis
Compare your current controls to PCI requirements to see where gaps exist. An affordable pentest at this stage often uncovers issues documentation reviews miss. - Remediate Issues
Fix identified weaknesses such as outdated software, weak firewall rules, or poor password policies. Our reports are delivered in about a week so teams can act quickly. - Complete Validation
Finish your SAQ or complete an audit for a Report on Compliance. Pentest results are a key requirement for passing Requirement 11.
Common PCI Compliance Mistakes To Avoid
Many businesses repeat the same PCI mistakes. Knowing them early helps avoid delays and penalties.
A common issue is underestimating scope. Logging servers or developer machines often get overlooked. Mapping everything that touches card data is critical.
Another mistake is treating compliance like a checklist. Running a scan and filling out forms is not enough. Real security requires manual testing.
Testing too infrequently is another problem. PCI requires annual testing and testing after major changes. Affordable pentesting makes regular testing realistic.
Weak passwords are still one of the most common attack vectors. Credentials like admin or simple passwords continue to show up during tests. Strong passwords and multi factor authentication make a big difference.
A Few Common PCI DSS Questions
Here are direct answers to common PCI questions.
How often do I need a PCI DSS pentest?
At least once per year and after any significant system change. Our pricing model makes repeat testing manageable.
What is the difference between a scan and a pentest?
Scans are automated and look for known issues. Penetration tests are manual and find complex vulnerabilities. PCI requires both.
Am I compliant if I use Stripe or Square?
Using these platforms reduces scope but does not remove responsibility. Your systems must still be secured.
How much does a PCI DSS pentest cost?
Traditional firms charge high fees and take months. We provide certified testing faster and at a lower cost. Contact us for a clear quote.
Ready to get a fast and affordable pentest that meets PCI DSS requirements. Affordable Pentesting delivers detailed reports from certified experts in about a week. Get a quote today and simplify your compliance process.
Get Your PCI DSS Pentest Quote
.svg)
