Confused by cyber threats? Cyber Threat Intelligence (CTI) is like getting an enemy's playbook before the game, letting you build a smarter defense against real attacks instead of just reacting to breaches. This guide breaks down what CTI is and how it helps you protect your business without breaking the bank.
Why You Need Cyber Threat Intelligence
Imagine you’re defending a castle. Random security alerts are just noise. Cyber Threat Intelligence is like a scout telling you exactly where the enemy will attack, so you know where to put your guards. It cuts through the chaos.
Instead of drowning in alerts, CTI helps you focus on threats that matter to your business. It turns raw data into simple answers: who is attacking, what tools they use, and why they're targeting your industry. This helps you make faster, smarter security decisions.

The CTI market is growing fast, expected to hit USD 55.7 billion by 2034, because businesses are tired of being a step behind. Attacks are getting smarter, and a proactive defense is no longer optional. You can discover more insights about the growing CTI market to see the trends.
Ultimately, CTI helps you use your limited time and budget wisely. By understanding specific threats, you can stop wasting money on generic defenses and focus on what actually protects your company.
The Four Levels of Threat Intelligence
Not all intelligence is the same. A CISO needs a big-picture view, while a security analyst needs technical details. Understanding the four levels of CTI ensures the right people get the right information at the right time.

Think of it like this: strategic is the 30,000-foot view for leaders, while technical is the ground-level detail for your tech team. Getting this right means your defense is coordinated and effective from top to bottom.
Strategic Intelligence for Business Leaders
Strategic intelligence is for your executives and board members. It answers the big "who" and "why" questions about threats, connecting them to business risk. It’s not about code; it’s about understanding the threat landscape.
This level helps leadership make smart decisions on security budgets and long-term planning. The CTI market is projected to reach nearly USD 57.9 billion by 2034, driven by this need for high-level insight. You can read the full research about CTI market trends to learn more.
Operational Intelligence for Security Teams
Operational intelligence focuses on the attacker's playbook: their tactics, techniques, and procedures (TTPs). This is for your security operations center (SOC) and incident response teams. It helps them understand how an adversary operates.
This intelligence is like knowing an opponent's signature moves. It tells you what tools they use and how they move inside a network. This allows your team to build proactive defenses against known attack methods.
Tactical Intelligence for Immediate Defense
Tactical intelligence is for your security tools, like firewalls and antivirus software. It consists of simple indicators of compromise (IoCs), like malicious IP addresses or malware file hashes. Think of them as digital fingerprints left by attackers.
Your security systems can use this information to automatically block known threats in real time. This type of intel has a short shelf life, but it’s essential for stopping the constant stream of common attacks.
Technical Intelligence for Deep Analysis
Technical intelligence is the most granular level, used by malware analysts and forensics experts. They dissect malware samples to understand exactly how they work. This deep dive uncovers unique characteristics that can be used to create highly effective, long-lasting detection rules.
These four types work together. Strategic guides the overall direction, operational prepares your defenders, tactical provides frontline defense, and technical stops sophisticated threats. This layered approach creates a truly robust security posture.
How the Threat Intelligence Lifecycle Works
Effective threat intelligence isn't a one-time report; it's a continuous cycle that turns raw data into actionable defense plans. This process, known as the threat intelligence lifecycle, ensures your team is always working with the best information possible.
Think of it like weather forecasting. Meteorologists follow a strict process of gathering data, analyzing it, and sharing the forecast. The CTI lifecycle has six key stages that repeat to keep your organization safe.
Stage 1 Direction and Planning
The process starts by defining your goals. What do we need to protect? Who are our likely attackers? This stage sets the scope and ensures every following step is focused on what matters most to your business.
Without clear direction, your team will waste time collecting useless information. Asking the right questions from the start makes the entire process more efficient and effective.
Stage 2 Data Collection
Once you know what you're looking for, you gather the raw data. This involves pulling information from a wide variety of sources, including internal logs, public forums, and industry threat feeds.
The goal isn't just to grab a ton of data. It's to collect relevant information that aligns with the goals you set in the first stage, creating a targeted and useful dataset.
Stage 3 Processing The Raw Data
Raw data is messy and unusable. The processing stage is where you clean it up and get it organized. This involves filtering out irrelevant information and formatting everything into a consistent structure.
This step is like a chef preparing ingredients before cooking. It turns a chaotic flood of data into a neat, organized dataset that's ready for analysis.
Stage 4 Analysis and Production
This is where your team connects the dots. Analysts review the processed data to find patterns and figure out what it all means. This is the step where raw information becomes true intelligence.
For example, an analyst might link a list of malicious IP addresses to a specific ransomware group targeting your industry. This provides the context needed to understand the threat.
Stage 5 Dissemination and Reporting
Intelligence is useless if it doesn't get to the right people in a way they can understand. The dissemination stage is about sharing the finished intel with stakeholders. This could be a high-level brief for your CISO or a technical alert for your security team.
The report must be clear, concise, and tailored to its audience. A technical report won't help your board, and a simple summary won't help your engineers.
Stage 6 Feedback and Refinement
Finally, the lifecycle comes full circle. After the intelligence is used, stakeholders provide feedback on whether it was useful and timely. This input helps refine the entire process for the next cycle.
This continuous loop ensures your CTI program gets smarter and more effective over time. It's also a key part of our guide on security incident response planning.
What Do You Actually Get Out of CTI?
So, what’s the payoff? The biggest benefit of CTI is shifting your security team from a reactive to a proactive stance. You start preventing fires instead of just putting them out.
This proactive approach means your team can stop chasing every minor alert and focus their time and budget on the threats that pose a real risk. It’s about working smarter, not harder.
Moving From Reactive to Proactive Defense
Without CTI, most security teams are stuck in a cycle of reacting to incidents after they happen. It's exhausting and inefficient. CTI flips the script by giving you foresight into an attacker's playbook.
It helps you anticipate attacker behavior, prevent breaches before they happen, and patch the vulnerabilities that are actively being exploited right now. This makes your defense much more effective.
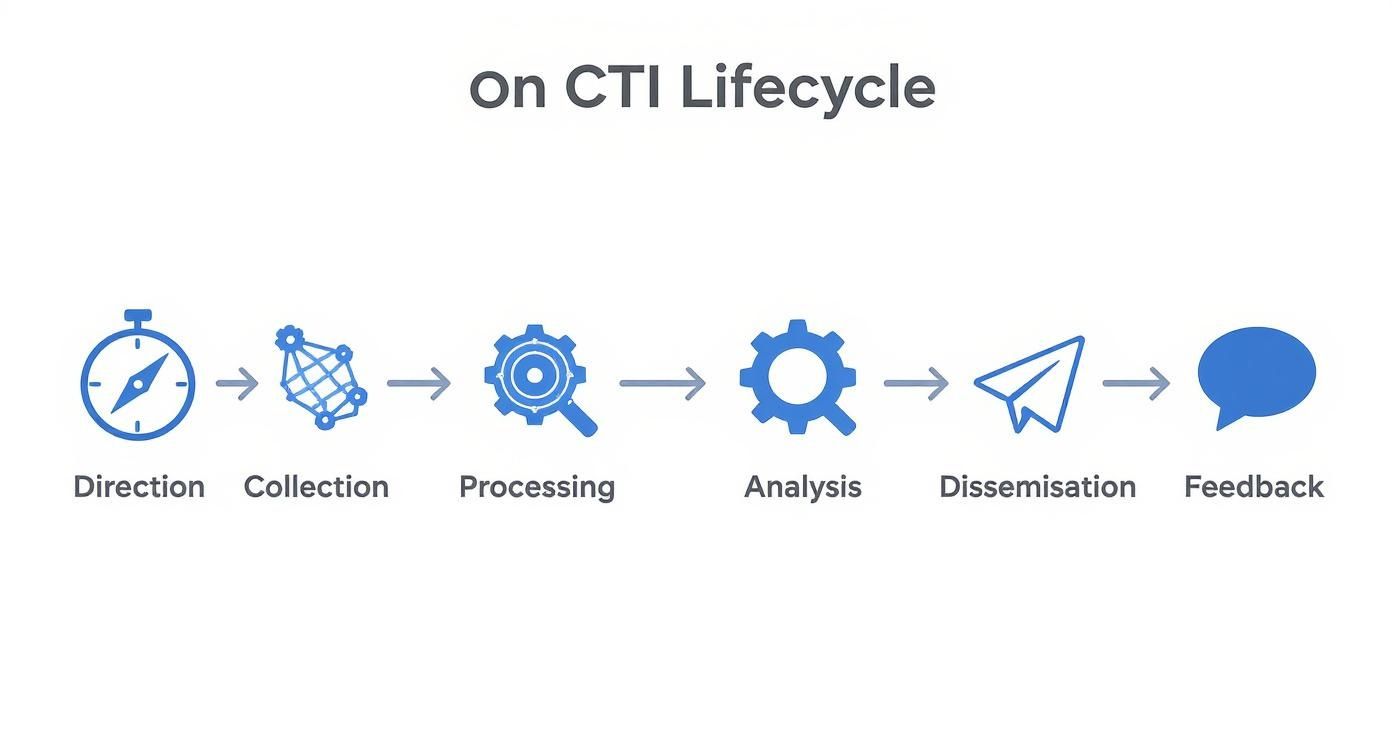
The process starts with clear goals and ends with feedback, ensuring your security strategy is always adapting to the latest threats.
Better Incident Response and Prioritization
When an incident does happen, CTI makes your response faster and more effective. Your team has context about who the attacker might be and what methods they use, allowing them to contain the threat quickly.
CTI also helps you cut through the noise of constant security alerts. It highlights the threats most relevant to your organization, so you can focus your resources where they will have the most impact.
Clarifying Your Unique Attack Surface
CTI is essential for understanding how attackers see your organization's digital footprint. It helps you find exposed assets and weaknesses that could be an easy entry point for an attack.
Our affordable pentests use this kind of intelligence to simulate realistic attacks. Our OSCP, CEH, and CREST certified pentesters deliver actionable reports in under a week, so you can fix what matters—fast.
Threat Intelligence in Real-World Scenarios
Theory is one thing, but seeing CTI in action is where its value really clicks. These real-world scenarios show how organizations use intelligence to shut down attacks and protect their business.

Let's walk through a few examples of how threat intelligence is used on the ground to prevent financial loss and reputational damage.
Example 1 Dismantling a Phishing Campaign
A financial firm sees a rise in suspicious emails targeting its accounting department. Using CTI, they discover it's a targeted campaign by a known cybercrime group. The intelligence reveals the group's tactics, infrastructure, and goals.
Armed with this intel, the firm's Security Operations Center (SOC) proactively blocks the malicious IP addresses and creates new email filters. This intelligence-led approach neutralizes the entire campaign. Learn more in our guide on what is a Security Operations Center.
Example 2 Fortifying Defenses Against Ransomware
A healthcare provider receives an intelligence report about a ransomware group actively targeting medical facilities. The report details the group's entire attack chain, including how they exploit unpatched VPN servers to gain access.
The hospital's security team uses this intel to immediately find and patch a vulnerable server on their network. By understanding the attacker's methods, they hardened their defenses against a specific, relevant threat.
Example 3 Protecting an E-Commerce Site
An online retailer subscribes to a threat feed that includes data on new credit card skimming malware. Their security systems automatically ingest this feed, updating their endpoint protection software to block the threat.
This is a simple but powerful example of how CTI can provide immediate, automated protection. The threat is stopped before a single customer's data can be compromised.
How to Start Your CTI Program
Starting a Cyber Threat Intelligence (CTI) program doesn't have to be a massive project. You can start small and build a practical program that delivers real value right away. The key is to begin with a simple plan focused on protecting what matters most.
First, define your goals. What are your most critical assets? Who are your most likely attackers? Answering these questions provides the focus you need to avoid drowning in useless data.
Setting Up Your Initial Framework
With your priorities straight, you can begin gathering intelligence without needing an expensive platform. Many organizations start with free or low-cost resources that provide immediate value.
Start with these foundational sources:
- Open-Source Intelligence (OSINT): Free threat data published by security researchers and government agencies.
- Industry Sharing Groups (ISACs): These groups deliver threat intel that is highly relevant to your industry.
As you plan, think about the people who will run your program. Exploring a comprehensive cybersecurity certification roadmap can help ensure your team has the right skills.
Integrating Intelligence and Growing Your Program
Once you have a steady stream of intelligence, plug it into your existing security tools. Your firewall, endpoint protection, and SIEM can all use this data to automatically block threats. See how this works with common network security monitoring tools.
The goal is to start small, get some quick wins, and prove the program’s value. A successful CTI program evolves over time. As your program matures, you can add new sources and integrate intelligence deeper into your security operations.
CTI Questions We Hear All The Time
Still have questions? Here are simple answers to some of the most common things we get asked about cyber threat intelligence.
What Is the Difference Between Data and Intelligence?
Threat data is just a list of raw clues, like malicious IP addresses. On its own, it’s just noise. Threat intelligence connects those dots to tell you who is attacking, why they're targeting you, and how they operate. In short, data is a fact; intelligence is the story that helps you make a smart decision.
Is CTI Only for Large Corporations?
Not at all. Any business can benefit from CTI. You can start with free resources like open-source intelligence (OSINT) feeds and industry-specific groups (ISAC). These provide tactical intelligence you can plug directly into your existing security tools to block known threats.
How Does CTI Fit With Penetration Testing?
They are a perfect pair. CTI tells you how real-world attackers would try to break into a company like yours. A penetration test then uses that intelligence to simulate a realistic attack. This makes the pentest much more valuable because you're testing your defenses against the threats you are most likely to face.
At Affordable Pentesting, our OSCP, CEH, and CREST certified experts use intelligence to model these real-world attacks. We find the vulnerabilities that matter most and deliver a detailed, actionable report in under a week without the high costs of traditional firms. Fill out our contact form to learn how we can help secure your business.
.svg)
